Locky, the biggest and most prevalent ransomware family known today, is in the midst of a change to how it spams victims, dropping WSF files and choosing to go with LNK files.
Since it was first discovered and up until recently, the group behind the Locky ransomware has been targeting users in three ways: via exploit kits, via macro-laced Office files, and with ZIP files.
By far, the most encountered spam distribution technique was the one spreading ZIP files. When users would unzip these files, they'd usually find all sorts of files inside, which, if executed, would install the Locky ransomware.
New Locky distribution trend emerges
Historically, these ZIP files have distributed JS files, HTA files, and most recently WSF files. According to the Microsoft Malware Protection Center, the most recent trend in Locky ZIP spam is the usage of LNK files.
"We observed that the Locky ransomware writers, possibly upon seeing that some emails are being proactively blocked, changed the attachment from .wsf files to shortcut files (.LNK extension) that contain PowerShell commands to download and run Locky," researchers noted yesterday.
The switch to LNK files is recent and seems to be tied to the demise in Nemucod detections. Nemucod is a "malware downloader," an intermediary step between the malicious ZIP file and the actual Locky infection. The Locky gang used Nemucod to test infected computers for sandboxed environments and to get boot persistence before downloading their ransomware.
The Locky group deployed Nemucod for its Locky ZIP -> WSF spam campaigns, and the slowdown in Nemucod detections also confirms a change of tactics from the Locky group.
Locky group using Windows "shortcuts" to download ransomware
LNK is the file format of Windows "shortcuts." LNK files have been used in malware distribution in the past, and Locky is not the first malware to use this trick.
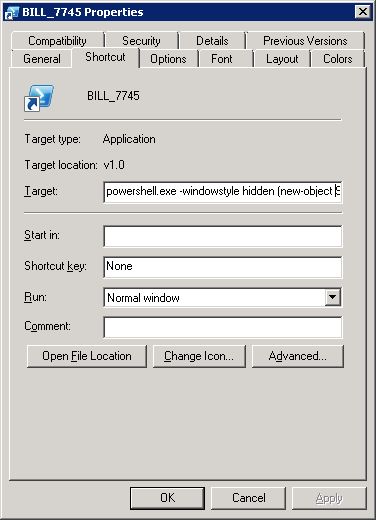
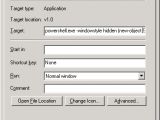
The LNK files install malware by linking to an application everyone has on their computer. In this case, it's Windows Powershell, an OS-level scripting and automation language included in all Windows versions, which is often abused by malware distributors to automate the operations needed to install malware without needing user interaction. Basically, Powershell scripts are like batch scripts on steroids.
The Locky actors are creating a shortcut to the user's local Powershell utility, and passing preset parameters and commands, as in the image below.
Since LNK (shortcuts) can have different icons, the user is easily tricked into double-clicking and running the file, starting the pre-packaged Powershell script.
Microsoft researchers said they've seen LNK campaigns spread Locky's newest version, the one that locks users' files with the ODIN extension.
Research from Proofpoint has revealed that Locky spam accounted for 97 percent of all spam campaigns spreading malicious email attachments, so keeping up to date with the latest Locky distribution tricks is a must.

 14 DAY TRIAL //
14 DAY TRIAL //