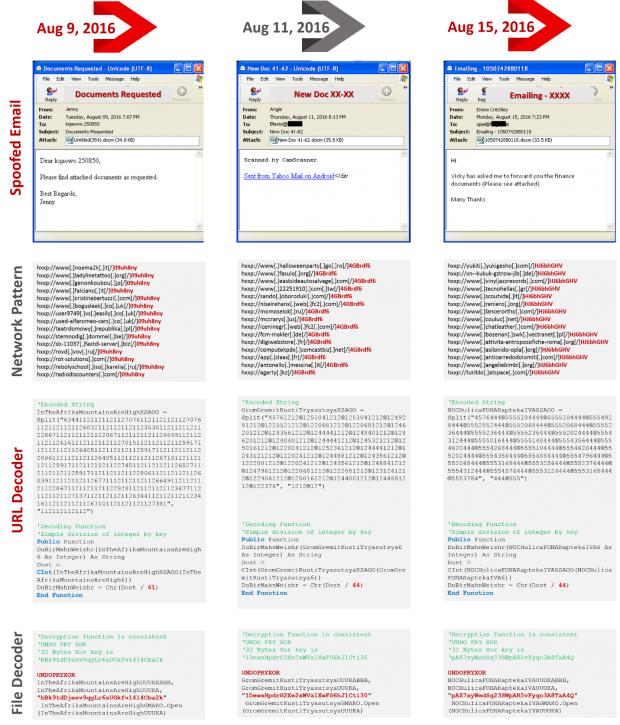
The criminal group behind the Locky ransomware switched distribution tactics at the start of June, abandoning JS-based droppers for malicious Microsoft Office documents with the DOCM file extension.
Since it appeared, if there was one common feature in all the Locky spam, it was the fact that Locky used a boobytrapped JavaScript file packed inside a ZIP file, which the crooks sent to potential victims via spam emails.
According to FireEye, starting with August 2016, the group uses macro scripts embedded in Office DOCM files. When the user opens these documents and allows the macro script to execute by "enabling editing," the script connects to an online server, downloads and installs the ransomware.
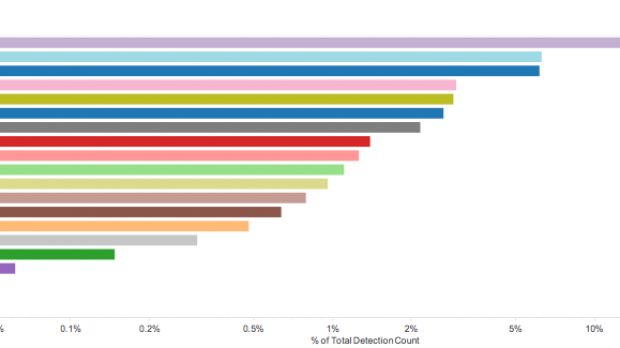
Multiple Locky spam campaigns hit various countries around the world
FireEye says that this new wave of Locky spam has impacted victims from all over the world, not just a specific area. Of course, some countries are more targeted than others, but everyone is spammed in the end.
According to statistical data gathered in the first half of the month of August, users in the US, Japan, Republic of Korea, Thailand, and Singapore received the most spam.
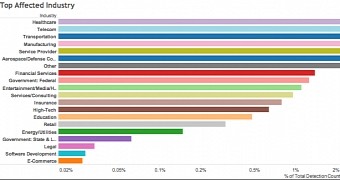
Based on the email addresses at the receiving end of all this spam, researchers say that the healthcare sector was the most targeted, no doubt because of the recent high-profile cases where the infected institutions eventually ended up paying the ransoms.
Other targeted industries included the telecom field, transportation, manufacturing, and general services.
Dridex distribution stopped in the meantime
It's been known for a while that the group distributing the Locky ransomware uses the same C&C infrastructure utilized by the infamous Dridex gang that distributes the eponymous banking trojan.
FireEye says that distribution of Dridex payloads seems to have stopped altogether. Dridex was famous for using Office documents and macro scripts to infect hosts, just like the new Locky method.
These recent Locky spam campaigns come in different waves, each one using a different payload, but FireEye says it detected a common pattern among all, which shows the professionalism of the people behind this operation, and why they managed to make victims for so many years without getting caught.
 14 DAY TRIAL //
14 DAY TRIAL //