Security researcher MalwareHunterTeam tells Softpedia that the infamous Locky ransomware has returned today with a new spam campaign that's spreading a new version of the ransomware.
Last week, Microsoft's Malware Protection Center revealed that the group behind Locky had reduced its spam efforts and was testing a new distribution method that relied on small spam campaigns spreading booby-trapped LNK (shortcut) files.
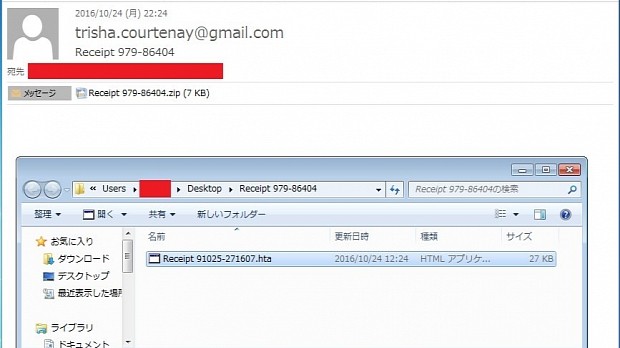
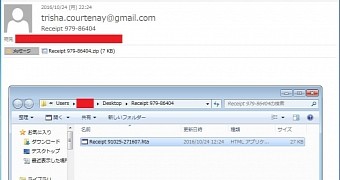
Over the weekend, Locky's creators have returned to their old tricks, and are now in the midst of a massive spam campaign that spread zipped HTA, WSF, and JS files, which are Locky's classic infection methods. An analysis of the email lures used for this spam campaign is available via My Online Security.
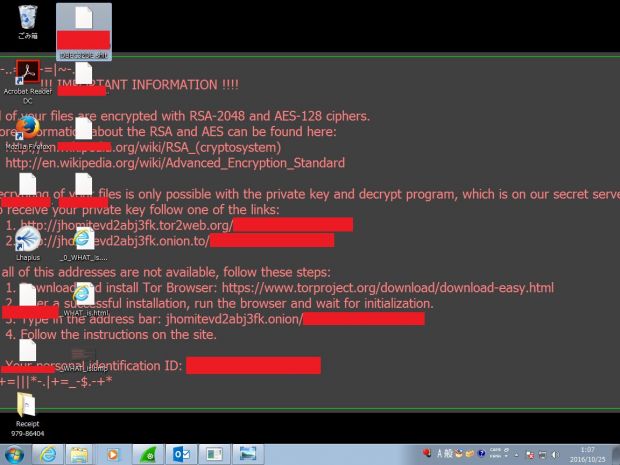
Locky pushes out new file encryption extension
The most visible change in this version of Locky is the extension it appends at the end of encrypted files.
The new extension is SHIT, and this is not the only salacious detail observed by researchers, who say the ransomware calls back home, to a server file named "linuxsucks.php."
For example, a file named photo.png would become [random_characters].shit. Previously, Locky had used extensions such as LOCKY, ZEPTO, and ODIN.
As for the random file names, MalwareHunterTeam said the format is "8-4-4-4-12.shit, where the first 8-4-4 characters are unique for infection, and the last 4-12 is unique for the file."
New Locky variant pushed to victims via worldwide spam campaign
According to MalwareHunterTeam, infections came in quick and fast. The researcher detected these infections via ID-Ransomware, a free website his team had created, which helps victims of ransomware infections.
People that had their computer locked by ransomware, can access this website, upload a copy of the ransom note and one of the encrypted files, and find out the name of the ransomware that locked his PC, and if there's a free decrypter available to recover their files.
In a matter of six hours, MalwareHunterTeam tells Softpedia, that the new Locky S**T version has made victims in Germany, France, Serbia, the UK, Poland, Saudi Arabia, Finland, Bosnia and Herzegovina, Denmark, Turkey, Romania, Spain, the US, Gabon,Dominican Republic, Czech Republic, Canada, Argentina, South Africa, Honduras, and Venezuela. (in this order).
To better understand the rate at which new countries showed up in ID-Ransomware's backend, as your reporter was talking to MalwareHunterTeam, one new country with S**T ransomware infections popped up every five minutes.
Not a new ransomware, but a Locky variant
Researchers such as MalwareHunterTeam, TMMMalAnalyst, Techhelplist, Peter Kruse, SecGuru, operations6, and Racco42 have identified this ransomware as a Locky variant, and not as a new ransomware family.
They haven't had the time to look at this version's source code in depth, but a researcher named Techhelplist has identified the first change, which is a modification in Locky's DLL point.
LockyDump, a tool created by Cisco researchers to extract Locky ransomware configuration files, was able to extract configs from Locky S**T samples, which means this is a valid Locky variation.
Furthermore, the standard desktop wallpaper used by Locky S**T is also identical to previous Locky screens. Serbian security researcher GrujaRS also recorded a video of a Locky S**T infection in progress, which you can also view below.
 14 DAY TRIAL //
14 DAY TRIAL //