Security researchers have discovered a new self-propagating trojan targeting Linux systems, which uses unsecured Redis database servers to spread from system to system.
Discovered by Russia-based antivirus maker Dr.Web, the trojan, named Linux.Lady, is one of the few weaponized Go-based malware families.
Researchers say that Linux.Lady is written using Google's Go programming language and mostly relies on open source Go libraries hosted on GitHub.
Over 30,000 Redis servers may be vulnerable
The trojan infects systems by connecting to misconfigured Redis database servers for which administrators have forgotten to set a password. According to a recent Risk Based Security report, there are over 30,000 Redis servers available online without a password.
The initial entry point is not the Linux.Lady trojan, but a smaller trojan called Linux.DownLoader.196, which, in turn, downloads the main payload after securing a foothold on the infected machine.
After the smaller trojan launches Linux.Lady into execution, this latter malware collects information about the infected system and sends it to a C&C server.
The collected data includes details such as the computer's current Linux version, the Linux OS family name, the number of CPUs, the number of running processes, and their names.
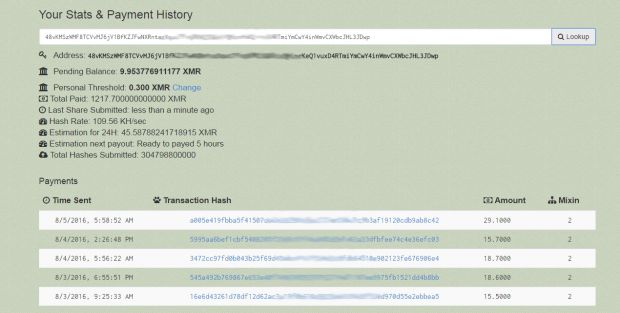
Linux.Lady mines for the Monero digital currency
Once the C&C server is informed of the creation of a new bot, it sends over a configuration file, which Linux.Lady uses to start a cryptocurrency mining program that generates digital currency for the crook's account.
The trojan mines for a cryptocurrency named Monero, the same one used by the author of the PhotoMiner worm that self-propagated through vulnerable FTP servers.
Just like PhotoMiner, Linux.Lady comes with self-propagation features. The trojan includes a function that detects the IP address of the infected computer, scans the local network, and probes for other vulnerable Redis servers that don't feature a password on the admin account.
Once it finds one, the infection process starts from zero, authenticating on the Redis server, downloading Linux.DownLoader.196 and adding it to a cron job.
 14 DAY TRIAL //
14 DAY TRIAL //