In the last three months of 2015, the DDoS landscape evolved with new types of attacks, and an increased focus on leveraging Linux-based botnets to launch DDoS assaults.
According to Kaspersky Lab's DDoS Intelligence Report for Q4 2015, attackers got crafty and focused their efforts on finding new methods of launching DDoS attacks.
New DDoS attack vectors came to the forefront in Q4 2015
A few of these methods are RPC, NetBIOS and Sentinel services, which you can read more about in one of our previous articles.
Other types of DDoS attacks that got popular in the last three months are the ones carried out via WordPress sites, which were infected with malicious JavaScript code.
This code executes in the user's browser and makes a request to a predefined DDoS target, inadvertently transforming a website's visitor into a temporary bot in a larger WordPress-powered DDoSing botnet.
Of course, it wouldn't have been a good analysis of the DDoS landscape from Kaspersky if the company didn't mention the increase in DDoS attacks launched from infected IoT devices, of which we saw a few in the last months.
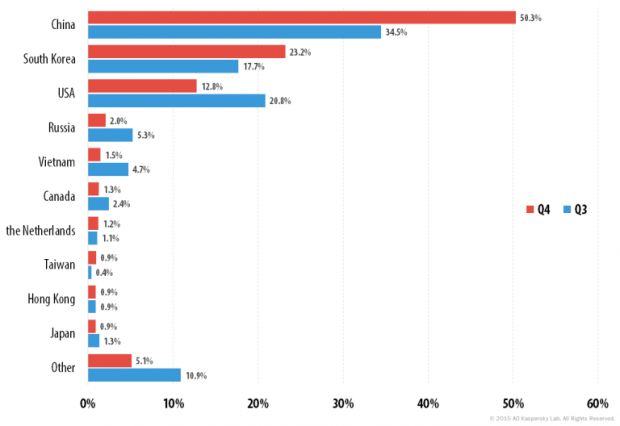
Half of all DDoS attacks were aimed at China
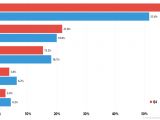
As or the numbers, in Q4, Kaspersky observed DDoS attacks launched against 69 countries, with more than half (50.3%) aimed at China. Second on that list is South Korea (23.2%) who leapfrogged the US (12.8%) who's now in third.
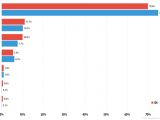
When it came to the source of the DDoS attack's C&C server, South Korea remained the leader, accounting for 59% of all the servers, followed by the US (11.5%), China (8.3%), Russia (5.5%), and Great Britain (2.6%).
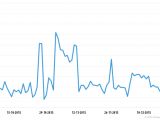
Most of these attacks were pretty evenly distributed across the last three months, but the busiest day was on November 2, when a whopping 1,442 attacks were recorded.
As in the previous quarters, the most popular attack method was the classic SYN flood, which accounted for 57%, followed by TCP floods with 21.8%, and classic HTTP floods with 15.2%.
Kaspersky says that 70% of all DDos attacks lasted less than a day, but it also recorded a 371-hour long attack (15.5 days), and another one of 320 hours (13.3 days).
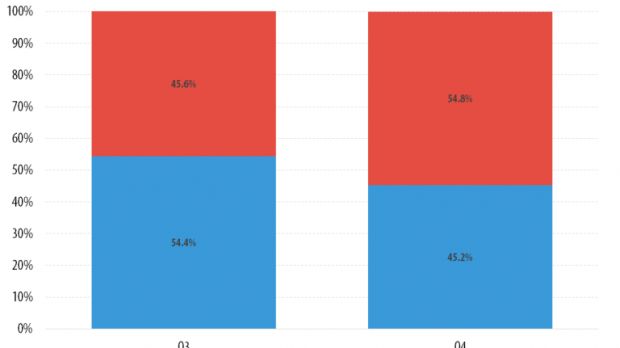
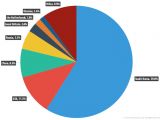
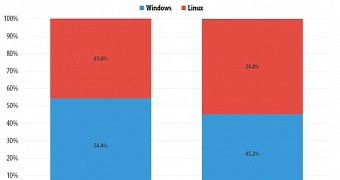
To blame for most of this useless traffic are Linux-based botnets, which become more prevalent, "beating" Windows for the first time and accounting for 54.8% of all the DDoSing bots.
 14 DAY TRIAL //
14 DAY TRIAL //