Lightspeed, a company based in Montreal, Canada, which sells point-of-sale (PoS) software to companies around the globe, has started notifying clients today of a security breach the company's engineers detected this week.
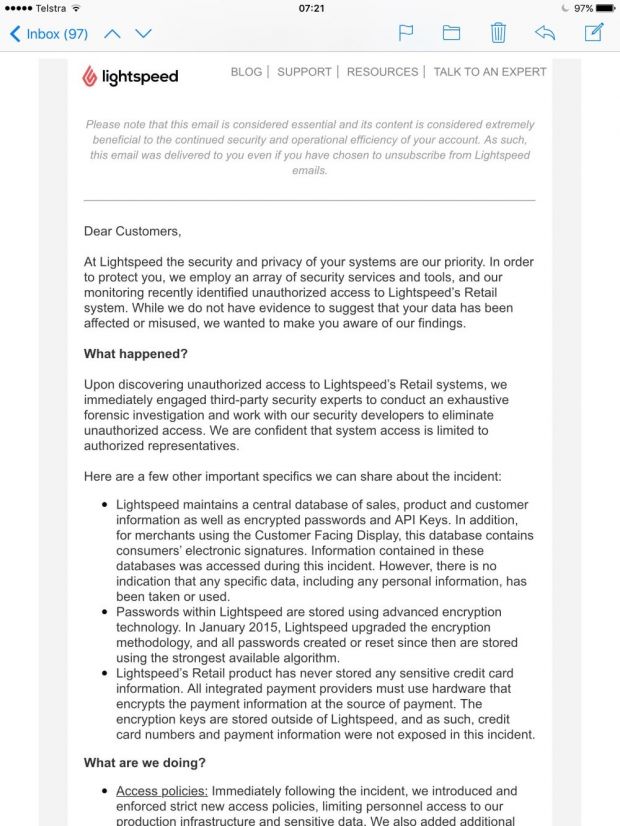
The PoS vendor says that an unknown attacker gained access to its Retail system, which stores data on companies that purchased Lightspeed PoS software to use with their PoS terminals.
No evidence the attacker exfiltrated any data
Attackers had access to a central database that held information on Lightspeed customers, but not their credit card transactions.
Lightspeed says the attacker accessed the database, but there's no evidence that they stole or misused any information from the servers. The company is now warning users to change their passwords. This is not a "forced" password reset, but only a recommendation, even though it would have been better if it was a "forced" password reset.
Potentially compromised data includes Lightspeed customer account information, API keys, electronic signatures, and encrypted passwords.
Lightspeed has also told customers that they'd changed the way passwords are encrypted in January 2015, opting for the "strongest available algorithm." The company has not been clear on the status of encrypted passwords created before January 2015, which may be crackable.
No credit card details exposed in the incident
Lightspeed has also made it clear that it does not store credit card information in its database. That information only travels from the PoS terminal to the bank and is never backed up by Lightspeed PoS software.
After learning of the incident, Lightspeed says it hired a cyber-security firm to investigate the incident.
Lightspeed is the second PoS software vendor to suffer a data breach this past month after Oracle's MICROS division experienced a similar incident.
The main suspects behind the MICROS breach are the Carbanak Russian cyber-crime syndicate, which previously stole over $1 billion from banks around the world using social engineering, targeted attacks, and custom malware.

 14 DAY TRIAL //
14 DAY TRIAL //