A cyber-espionage actor is targeting high-profile Libyans, infecting their Android smartphones with a remote access trojan (RAT) known as AlienSpy (JSocket, JBifrost, Unrecom, or Adwind).
The attacks started at the start of August 2016 after the threat actor, nicknamed Libyan Scorpions by Kuwait-based security firm Cyberkov, managed to compromise the Telegram account of a high-profile and influential Libyan figure.
Original victim could have stopped the attack before escalation
Cyberkov says the targeted individual received an alert from Telegram notifying him of a login from a Spanish IP address. The scared and non-technical victim, instead of changing his password, deleted the Telegram app from his smartphone, thinking the bad actor would be cut off as well.
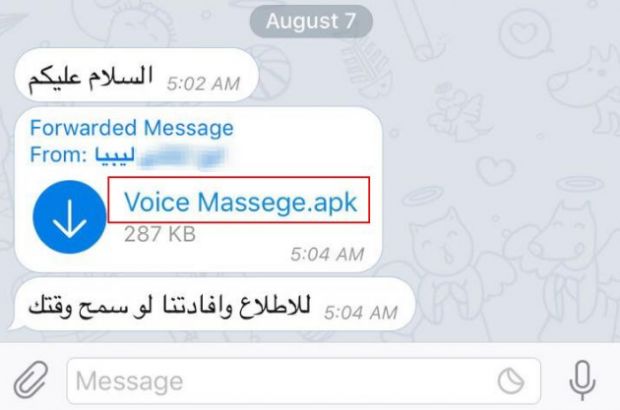
Instead, the crook was given free reign to start conversations with the victim's friends, luring them into downloading and installing an Android app named "Voice Massege.apk," claiming it would help them decode an important voice message.
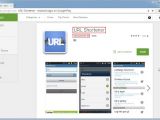
Cyberkov says this was a legitimate Android application downloaded from the Google Play Store and repackaged with the AlienSpy Android RAT. The original app's name is URL Shortener, identified as de.keineantwort.android.urlshortener.
C&C server tracked back to Lybia
Researchers who analyzed it discovered that the app's command and control (C&C) server led them back to a local Libyan IP address belonging to Libya Telecom.
The same IP was also used to host a dynamic DNS service, meaning the crooks were using this infrastructure as a hub for all sorts of malicious operations, not just to host stolen data.
"They [Libyan Scorpions] appear not to have highly technical skills but good social engineering and phishing tricks," the Cyberkov team noted about the group. "The threat actors are not particularly sophisticated, but it is well-understood that such attacks don't need to be sophisticated in order to be effective."
"Using malwares [sic] as weapon in an active warzone such as Libya, make the victims easy targets for assassination or kidnapping by tracking their physical locations and monitoring them day and night," researchers also said.

 14 DAY TRIAL //
14 DAY TRIAL //