A stealthy new backdoor was detected by FireEye's Dynamic Threat Intelligence (DTI) team, one that takes great care to cover its tracks and stay hidden on infected systems like no other malware before it.
Codenamed LATENTBOT, security researchers are reporting that this particular piece of malware has infected computers in countries such as the United States, United Kingdom, South Korea, Singapore, Canada, Peru, Poland, Brazil, and the United Arab Emirates.
There's no specific aim for these campaigns, and LATENTBOT has been seen active on computers from different industry sectors.
A complex installation process
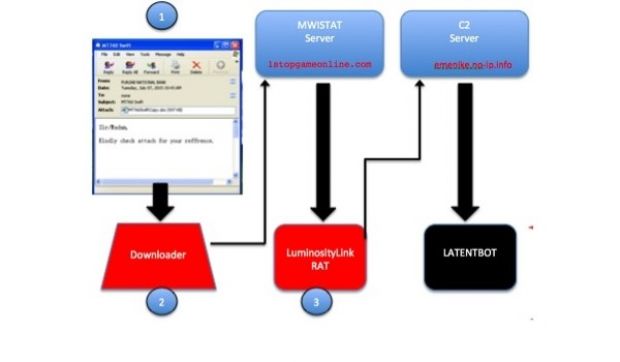
Most of the times, users get contaminated with LATENTBOT via email spam. Weaponized attachments infect the user's computer with a malware downloader, which then moves to secretly install the LuminosityLink RAT (Remote Access Trojan) on compromised PCs.
If certain conditions are met, a C&C server tells the RAT to install LATENTBOT. Unlike previous backdoor bots, this particular threat doesn't run on all systems and seems to stay away from older Windows versions (like Windows Vista or Windows Server 2008).
The LATENTBOT installation process is quite complex and designed for obscurity, going through six different stages, mainly to hide its true actions from reverse engineering.
Designed for silence, capable of complete destruction
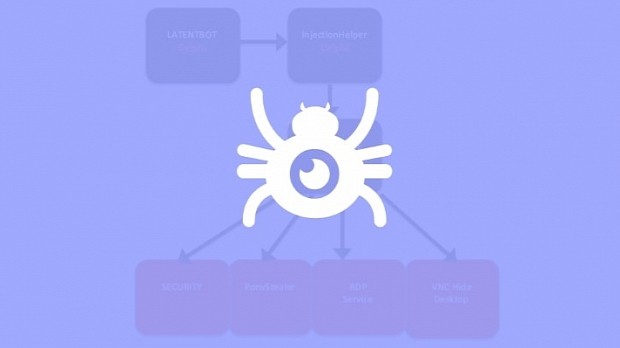
This special care for obscurity is also present in the bot's internal makeup and behavior that uses multiple layers of code obfuscation, removes data from the PC's memory as soon as it's not needed anymore, and hides applications in a different desktop.
Additionally, LATENTBOT was created using a modular infrastructure, meaning it can upgrade itself with new features. Some of these include the ability to work as ransomware by locking the user's desktop, by dropping the Pony malware on the victim's PC to steal password information, and even by wiping the victim's MBR (Master Boot Record), effectively ruining the computer's hard drive.
First signs of cyber-attacks using LATENTBOT were spotted in mid-2013. "It has managed to leave hardly any traces on the Internet," say FireEye researchers.
But there is good news. Despite LATENTBOT's special care for obfuscation and stealthiness, current antiviruses have caught up with it, and over half of the scanning engines available in VirusTotal are detecting it. They're labeling it as a generic trojan, and not a specific malware family, but at least they're detecting it.
"Although LATENTBOT is highly obfuscated, due to the multiple process injections performed, it is noisy enough to be easily detected in memory with a proper behavior-based solution," FireEye researchers conclude.
 14 DAY TRIAL //
14 DAY TRIAL //