Security researcher Sean Cassidy has developed a fairly trivial attack on the LastPass password management service that allows attackers an easy method for collecting the victim's master password.
Mr. Cassidy discovered that whenever LastPass sessions expire while the user is browsing the Web, LastPass shows this using notifications injected in a page's content. The subsequent login page and the two-factor authentication code, if enabled, are also displayed in the same way.
In terms of security, this is a big no-no, since it exposes users to Web injection attacks, commonly found in phishing attacks against users of Web-based banking portals.
Following an initial hunch, Mr. Cassidy explored this apparent weakness and discovered that attackers can exploit LastPass' tendency to show notifications and login popups inside a live Web page.
The researcher open-sourced the tool that carries out this attack
Mr. Cassidy developed a tool, which he also published on GitHub, called LostPass, which would be able to automate a simple phishing attack against LastPass users and harvest their password vault.
According to Mr. Cassidy, the only thing attackers need to do is to reroute users to a legitimate website that's vulnerable to XSS (cross-site scripting) attacks.
On these legitimate, yet vulnerable websites, the LostPass tool will use the XSS flaw to detect if a user has LastPass installed on his computer, log him out using a known CSRF issue, and then insert a notification asking the user to log into his account once again.
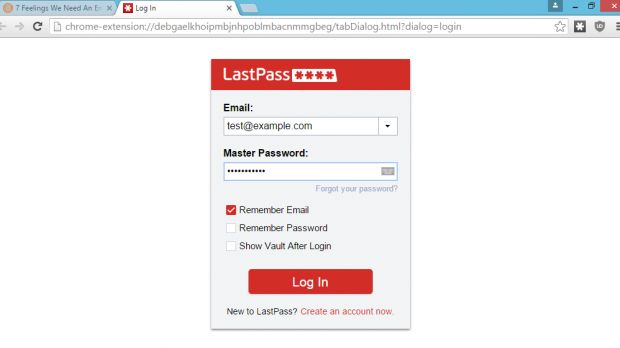
When the user clicks on this notification, a pixel-perfect LastPass login page appears, and when the user enters his credentials, they'll be logged on the attacker's server.
Attacker can intercept 2FA codes
Additionally, the attacker can even check these credentials against the LastPass API, verify their accuracy, and even ask the user for the two-factor authentication code if this feature is turned on.
If everything is correct, and all the codes verify through, using the same LastPass API, an attacker can collect any data from the user's account he wants, including the password vault.
Mr. Cassidy says that LostPass works only with Chrome browsers, since Firefox and other browsers show the LastPass login screens via browser specific popups. Cassidy says that he's working on experimental support for Firefox. LostPass was also tested with LastPass' most recent version, the 4.x series.
LastPass was notified but did not address the issue properly
The security researcher contacted LastPass last November. The company said they "confirm this is a phishing attack, not a vulnerability in LastPass." The company tried to fix this issue by warning users when they type in their master password into a website, but Cassidy said this was pointless since the warning was also a Web injection and can be intercepted and disabled by the attackers.
For now, this attack is also made easier in Chrome by the fact that attackers can register domains like "chrome-extensions.pw" that resemble the Chrome extensions management section, all without being warned by the browser.
In Firefox, Mr. Cassidy is working on a method that draws the OS-specific popups inside a page using HTML and CSS, making the user think he's entering the data into a LastPass window, when the data is actually entered inside the Web page.
Some mitigation techniques
To mitigate against his own attack, Mr. Cassidy recommends that users never re-enter LastPass credentials inside the browser, and use the main application to authenticate again.
Additionally, he also says that turning on IP restrictions for the LastPass paid version is better than using 2FA protection. Furthermore, users should also disable mobile logins, and log all logins and login failures.
Mr. Cassidy will be presenting his findings today at the ShmooCon security conference. A live stream will be available here.
 14 DAY TRIAL //
14 DAY TRIAL //