After yesterday security researchers from Bitdefender discovered the Eleanor trojan targeting Macs and opening a backdoor using Tor, today it's ESET's turn to reveal the existence of a similar backdoor trojan that also uses a Tor2Web service to steal Keychain passwords.
Named Keydnap and detected as OSX/Keydnap, this trojan is a new arrival on the Mac malware scene, first seen this past May (internal version 1.3.1), and later in June (version 1.3.5).
The malware's mode of operation is very simple, even if the infection chain is drawn out in several steps.
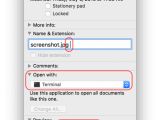
Keydnap dropper disguised as image or text files
Everything starts when users receive an email that contains an archive. Unzipping this file drops at first glance either an image or a text file. In reality, there's a space after the file's extension, meaning the file will run in the Mac terminal. This file is a Mach-O executable that uses a fake icon.
When executed, this file runs its malicious behavior and then shows an image if it's trying to pose as a picture, or a text pad, if it's trying to pose as a text file.
The malicious behavior is a series of operations ran in the console. The file first downloads another component, which is the actual Keydnap backdoor. It then executes the backdoor, which installs itself as LaunchAgent to get boot persistence, and then it downloads the image/text file it was posing as and shows that to the user.
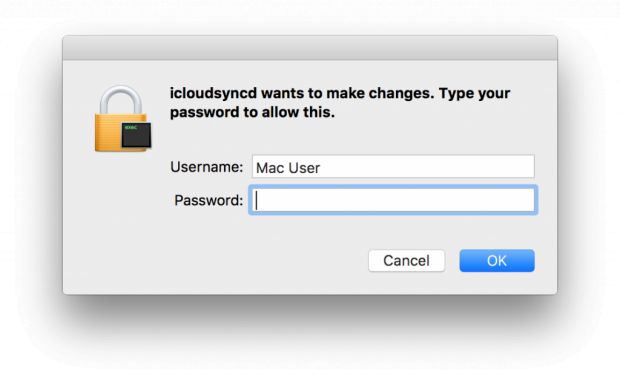
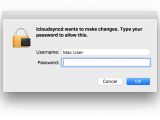
After this, the malicious behavior moves to Keydnap, which runs under the current user, but also tries to get root privileges by asking the user for their credentials using a popup.
Keydnap seems to be targeting security researchers
Keydnap then dumps the content of the Mac Keychain using the code of a GitHub project called Keychaindump and opens a link to a TOR website employing the onion.to Tor2Web proxy. The Keychain's content is sent to the C&C server via HTTPS.
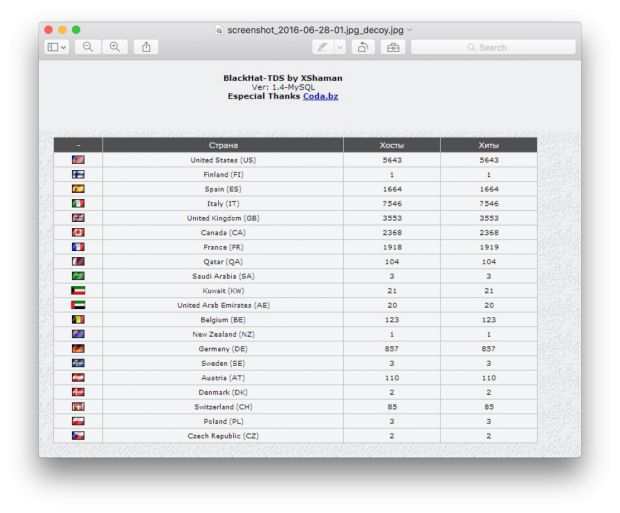
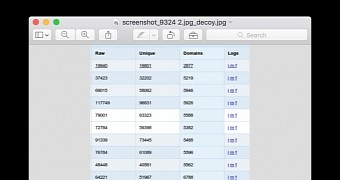
ESET has detected two C&C servers until now and says that, based on the decoy images the trojan shows to users in its early stages of infection, Keydnap might be after security researchers.
The decoy images, in many Keydnap instances, are pictures of botnet C&C control panels, something that only infosec professionals would be interested in.
Besides stealing passwords from the infected Mac, Keydnap can also download and execute files from a remote URL, download and execute Python scripts, execute shell commands and report back results, and update the backdoor with a new version.
"There are a few missing pieces to this puzzle. We do not know at this point how Keydnap is distributed. Nor do we know how many victims there are out there," ESET's Marc-Etienne M.Léveillé writes. "Although there are multiple security mechanisms in place in OS X to mitigate malware, it’s possible to deceive the user into executing non-sandboxed malicious code by replacing the icon of a Mach-O file."
 14 DAY TRIAL //
14 DAY TRIAL //