The usage of a rather simple keylogger malware has gone through the roof after its builder got leaked online last summer, Palo Alto Networks researchers have found.
KeyBase is a spyware family that can capture keystrokes, steal data from the user's clipboard, and take screenshots of the victim's desktop at regular intervals.
The malware was created in February 2015 but was seen for the first time in June when the same Palo Alto researchers stumbled upon an unprotected server (control panel) where KeyBase was sending its screenshots.
KeyBase's author stopped developing the malware last summer
Caught red-handed, its author promised to stop working on the malware, closed down the website from where he was selling KeyBase for $50 / €45, and abandoned the project.
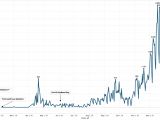
At that time, Palo Alto reported seeing 295 unique KeyBase samples and over 1,500 different KeyBase connections sending data back to control panels.
Shortly after having the veil lifted from KeyBase's operations, the malware's builder was leaked online and quickly made its way into all the main underground hacking forums.
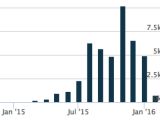
New KeyBase wave infected 933 Windows computers
Eight months later, Palo Alto is now reporting seeing over 44,200 KeyBase sessions coming from over 4,900 different KeyBase instances. It appears that the hacking community took over from the author and continued to develop KeyBase, branching out thousands of different variants.
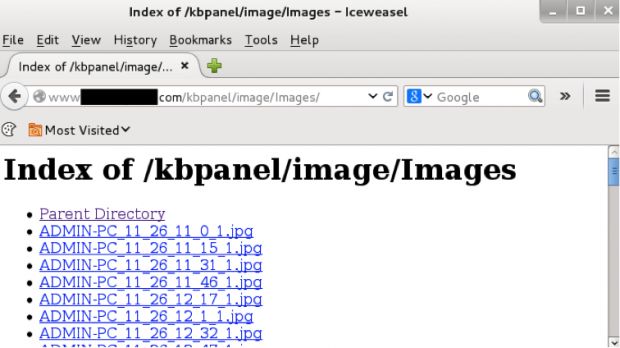
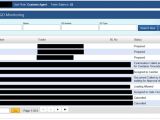
Researchers also discovered that while KeyBase's control panel was secured with authentication, the folder in which images were sent for storage was not, meaning that after all this time, they could easily put together a simple script and find all the KeyBase panels available online.
Using this simple method, Palo Alto staff discovered 62 Web domains where the KeyBase control panel was installed, 82 different control panels, and 125,083 screenshots from 933 Windows computers.
Of all infected computers, 216 were workstations in corporate environments, 75 were personal computers, and 134 were used for both. 43 of the 933 computers also included details from more than one user, meaning they were shared assets, used by multiple family members or work colleagues.
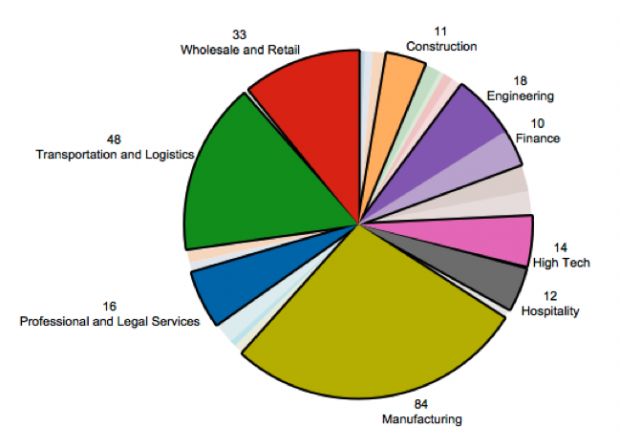
Attackers targeted the manufacturing industry
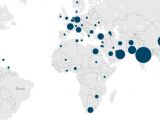
After analyzing most of the screenshots, researchers feel confident they managed to narrow down most of the attacks to a few campaigns. They say that most KeyBase infections are found in India, China, South Korea and the United Arab Emirates.
Additionally, the attackers focused their efforts on a wide spectrum of targets, but a few industries stood out. These included the manufacturing sector, companies activating in the transportation and logistics field, and the wholesale and retail industry.
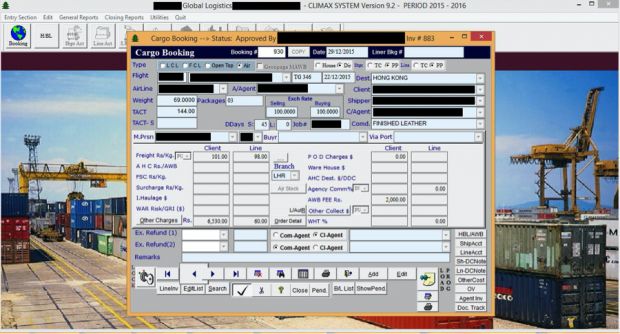
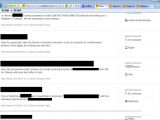
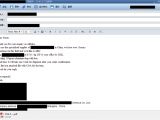
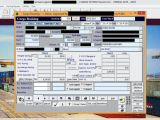
Taking a look at the screenshots, researchers discovered images depicting banking portals, invoices, blueprints, video camera feeds, email inboxes, social media accounts, financial documents, booking software, and many more.
Dummy hackers infected themselves as well
In the original KeyBase report, Palo Alto revealed that the malware's creator managed to infect himself during the keylogger's tests, and had his activities recorded through screenshots and then sent to the Web control panel.
This apparently happened again, and 16 of the actors behind this new wave of KeyBase infections also managed to infect their computers. The screenshots saved from their PCs shows that while a few were just curious script kiddies, some of the other hackers were actually professionals involved in highly-targeted campaigns.
In spite of the fact that KeyBase is a well-known and easy-to-detect threat, because its code is available to anyone, it means that the threat could evolve at any moment into something unpredictable and extremely dangerous.
The best way to stay safe is to avoid unsolicited or spam email, the most common method through which KeyBase infects its victims.
 14 DAY TRIAL //
14 DAY TRIAL //