The Kelihos botnet, sometimes also referred to as Waledac, has been adding new bots all summer and started shifting operations from spamming "pump-and-dump" campaigns to delivering ransomware and banking trojans, security researcher MalwareTech has discovered.
Kelihos is one of those old botnets created many years ago, which somehow has managed to avoid quite a few takedown attempts and has come back to life, just like Ramnit.
Discovered in 2008, Kelihos has been one of the main sources of pharma and pump-and-dump spam, even as recently as 2016. While spam filters got better at identifying these types of threats, the business behind these criminal activities also started to die down.
The veteran operators behind Kelihos are not your regular script kiddies, and they too saw this change in the underground cyber-crime market.
Kelihos size triples in a matter of hours
According to MalwareTech, who owns and operates the Botnet Tracker project, Kelihos operators have shifted their focus to the most lucrative cyber-crime operations around these days: ransomware and banking trojans.
Leveraging telemetry data obtained from his botnet tracker, the researcher reports that, at the end of June, Kelihos started spreading the WildFire ransomware.
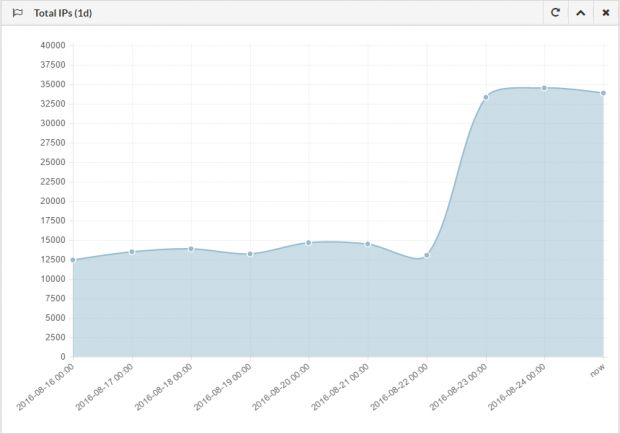
While for many weeks the botnet's size was steady at a lowly 8,000 infected machines, MalwareTech says the botnet received a big boost between July 9 and 11, when its size almost doubled to 13,000.
About the same time, the botnet dropped WildFire, which it had been spamming for some weeks and also started delivering other malware families, including an unspecified Zeus-based banking trojan.
This past Monday, on August 22, the botnet's size grew almost three times from 12,500-13,000 machines to a whopping 36,000 bots, all in a matter of hours.
Kelihos shifted focus to ransomware and banking trojan spam
The source of the new bots is currently unknown, and it can be anything from infected web servers to regular desktops. What MalwareTech was able to discover was that this was not a targeted campaign.
All the new Kelihos bots were randomly spread across the globe, with the most in low-income, high-population countries such as Turkey, Mexico, India, Iran, Brazil, and Peru.
"It’s likely that spamming the Wildfire ransomware was the Kelihos operator testing the water and now will likely joined [sic] the rest of the major spam botnets in the continued spamming of ransomware and banking trojans laced emails," MalwareTech noted. "I’d not be surprised if we continue to see further increases in infections as the operator expands the botnet to accommodate higher volumes of spam."
Gotta say Kelihos is doing very well for a botnet that has been declared dead on 3 different occasions by multiple security companies. — MalwareTech (@MalwareTechBlog) July 14, 2016
Huge increase in Kelihos infections this week, they likely found a new distribution method now Nuclear is gone. pic.twitter.com/iab7D7Q7st — MalwareTech (@MalwareTechBlog) July 14, 2016

 14 DAY TRIAL //
14 DAY TRIAL //