Kaspersky has confirmed today that the malware samples leaked on GitHub over the weekend by The Shadow Brokers are the real deal, and they have also presented similarities to the malware samples they analyzed from the Equation Group back in February 2015.
The devil is in the details, they say, and for this particular case, Kaspersky Lab's Global Research & Analysis Team (GReAT) says the principal factor that led them to this conclusion was the presence of RC5 and RC6 encryption algorithms inside the malware dumped by The Shadow Brokers.
Kaspersky notes that, during the past years, only the Equation Group has used these two algorithms inside their malware.
Clues: RC5, RC6, and coding patterns
During their initial analysis of the Equation Group malware, Kaspersky says it found 20 different malware samples where the crooks used RC5 and RC6 code. They found 347 difference malware samples in The Shadow Brokers data dump.
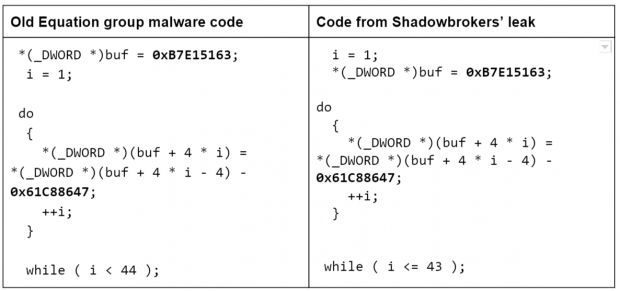
Furthermore, the security vendor's team also discovered coding patterns in the dumped malware unique to the way the Equation Group wrote its hacking tools, and unique to it alone. The technical explanation is as follows:
“ Inside the Equation group malware, the encryption library uses a subtract operation with the constant 0x61C88647. In most publicly available RC5/6 code, this constant is usually stored as 0x9E3779B9, which is basically -0x61C88647. Since an addition is faster on certain hardware than a subtraction, it makes sense to store the constant in its negative form and adding it instead of subtracting. ”
The company's GReAT team says "with a high degree of confidence" that the malware samples dumped online by The Shadow Brokers are related to the malware used by the Equation group.The Shadow Brokers are currently running an open auction for the rest of the Equation Group malware. The group dumped 347 malware samples as a free preview and is also taunting another set of hacking tools, which it will release to the person who wins the auction.
You can find more details about the auction and the way it's being handled in our original report.

 14 DAY TRIAL //
14 DAY TRIAL //