A new trojan discovered by Palo Alto Networks uses security software installed on the user's computer to side-load DLLs needed to install itself.
This new trojan was named Bookworm by Palo Alto's staff, which also observed some similarities with the PlugX RAT.
For now, Palo Alto reports that the trojan has been seen in the campaigns of an advanced persistent threat (APT) group activating only in Thailand.
A layered approach to malware delivery
As for its internal structure and MO, Bookworm seems to be part of the new, rising trend of modular malware, malicious threats that slowly install themselves in multiple steps to avoid detection, while also using a remote C&C server to control what components to load based on the profile of infected targets.
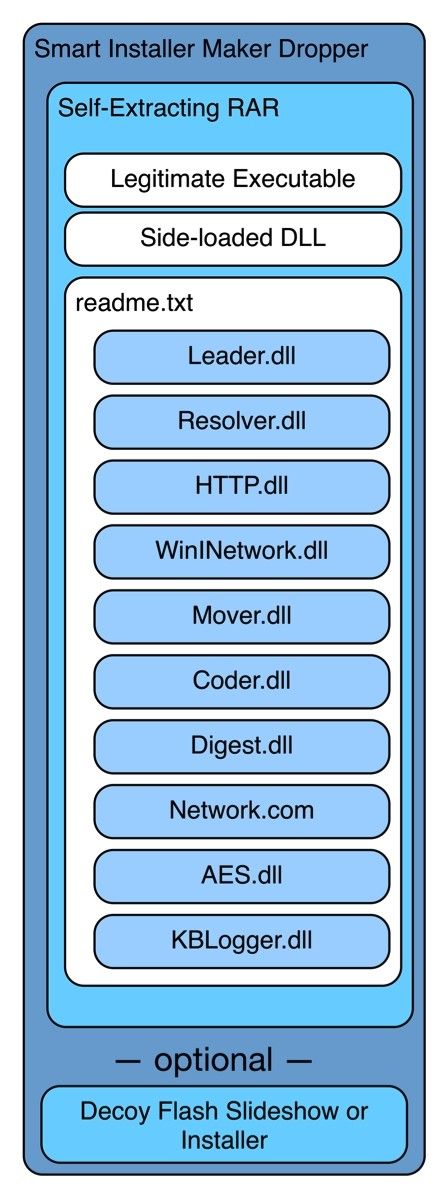
The internal architecture of a Bookworm trojan is simple. Multiple malicious DLLs are encrypted using an XOR algorithm and bunched together into a readme.txt file.
This readme.txt file is then put together with clean executables and some DLLs into a self-extracting RAR archive, which in turn is encapsulated with the Smart Installer Maker, an application for building installation packages.
The installer this application produces is the one that hackers are distributing. When executed, the installer triggers the self-extracting hardware that unloads the malicious readme.txt, the clean DLLs, and the clean EXE.
The trojan uses security products to install itself
After the installer finishes, it also automatically launches the clean EXE it just extracted. This executable starts to look for executables from Microsoft Malware Protection (MsMpEng.exe) and Kaspersky Anti-Virus (ushata.exe).
When it finds one, it side-loads the clean DLLs into these executables and uses the permissions of those applications to install itself as a Microsoft service.
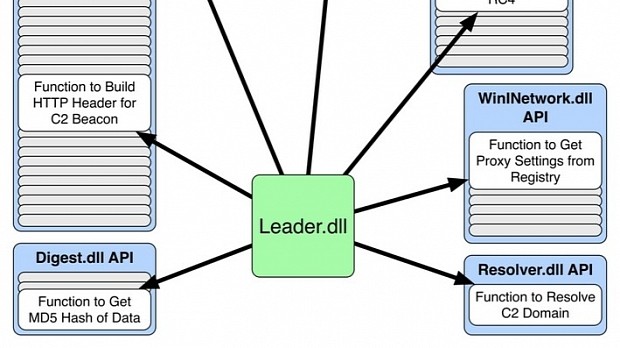
From here on out, Bookworm has all the permissions it needs to extract other modules from the readme.txt file, start communications with its C&C server, load other modules, and send stolen data to the C&C server.
Palo Alto researchers did not mention what other modules can be downloaded. They were hindered in their research by the fact that Bookworm used at least four encryption algorithms when talking to its C&C server (RC4, AES, XOR, and LZO).
 14 DAY TRIAL //
14 DAY TRIAL //