Telemetry data recorded by the Solutionary Security Engineering Research Team (SERT) reveals that, during the last quarter of 2015, malware numbers were up, Web reconnaissance events were down, and the ShellShock bug was still exploited, even a year and a half after a patch was released.
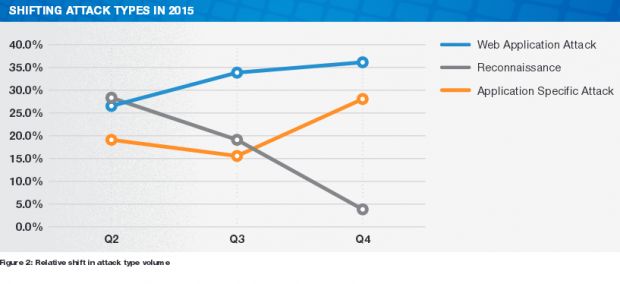
The first thing that Solutionary's data showed was the fact that Web reconnaissance scans were down during the past three months. These scans are usually employed by attackers to scan for vulnerable systems and are generally used by security products to identify potential threats against their clients.
While this is a good thing, the rest of the report doesn't follow this trend, and Solutionary has quickly pointed out that malware was up during the past quarter, with virus and worm numbers going up 236% compared to Q3.
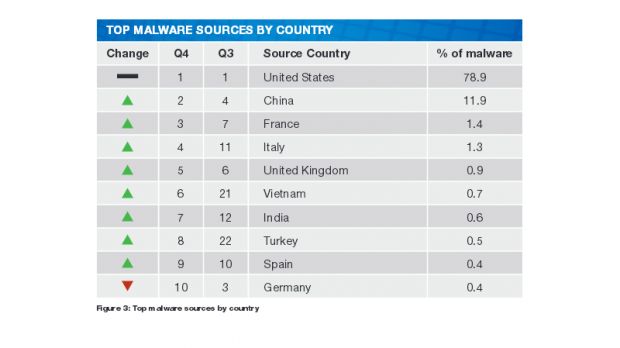
The US accounts for almost four-fifths of all of today's malware
Ransomware was also slightly up, but this was to be expected by any IT employee following the infosec community. Solutionary reports that most ransomware infections originated from Russia.
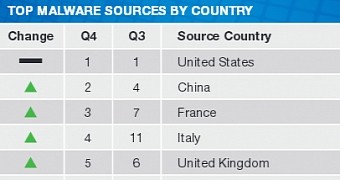
The top 10 sources of malware during the past three months were the US, which accounted for 78% of all the malware delivered during Q4, followed by China, France, Italy, the United Kingdom, Vietnam, India, Turkey, Spain and Germany.
Additionally, Solutionary has also noticed an increase of 77% of attacks leveraging the ShellShock vulnerability, mainly deploying the Bashlite malware, aimed at CCTV cameras and other IoT devices.
Joomla zero-day accounted for most Web application attacks
But most violations recorded in Q4 2014 were Web application attacks that targeted vulnerabilities in Web-based software. They amounted to 41% of all the cyber-incidents recorded in the last quarter.
Out of all detected Web application attacks, most were leveraging the recently discovered Joomla zero-day vulnerability, CVE-2015-8562, which affected all Joomla CMS versions released in the past eight years.
This comes as no surprise, since Sucuri already reported two weeks after the zero-day was discovered that its firewall product was detecting over 16,600 attacks per day.
With such a huge attack surface, hackers had a field day, especially one named Muhmmad Emad, who accounted for the most Joomla attacks coming from a single source. Emad is known in hacking circles for defacing government websites and leaving anti-ISIS messages behind.
You can download and read the entire SERT Quarterly Threat Report Q4 2015 from Solutionary's website.
 14 DAY TRIAL //
14 DAY TRIAL //