Security researchers from Cylance have revealed details about a massive, six-year-old cyber-espionage campaign known as Operation Dust Storm that has most recently targeted Japanese critical infrastructure.
Security researchers are reporting on attacks against Japanese private and public organizations, among which there are a reputable automaker, the local Japanese subsidiary of a well-known South Korean electric utility firm, and a company from the oil and gas industry.
Cylance reports that, prior to shifting their focus against Japanese victims, the group also targeted organizations from the US, South Korea, China, and many European countries.
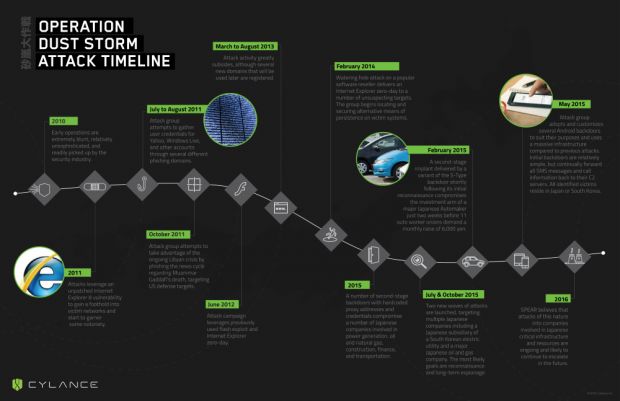
Operation Dust Storm started in 2010
First signs of the group were observed back in 2010, when they launched a series of unsophisticated and easy-to-spot attacks that leveraged zero-day vulnerabilities in Adobe Flash Player (CVE-2011-0611) and Internet Explorer (CVE-2011-1255) to distribute the Misdat malware.
Things evolved a year later when the attackers leveraged spam related to the Libyan crisis and Muammar Gaddafi's death to attack US agencies and the Uyghurs Chinese minority.
This time around, the group used a different Internet Explorer zero-day vulnerability (CVE-2012-1889), which was easy to pick up by most security vendors, just like in the first attacks.
Operation Dust Storm takes a break in 2013, comes back stronger
Attacks continued in 2012 but stopped towards the end of 2013, after Mandiant published a report on the activities of a Chinese-linked APT group codenamed APT1.
After this period of calm, Operation Dust Storm came back as strong as ever, and after a series of simple watering hole attacks via an Internet Explorer zero-day in 2014, it started shifting all its efforts on Japanese targets starting February 15.
This was also when the group started using for the first time a backdoor known as S-Type, and spying utilities targeting Android devices.
"The campaign has made use of malware that is customized for particular target organizations," Cylance researchers explain. "Attacks have employed spear phishing, waterholes, unique backdoors and unique zero-day variants, among others, to breach corporate networks and Android-based mobile devices."
More details can be consulted in the Operation Dust Storm report.

 14 DAY TRIAL //
14 DAY TRIAL //