Security researcher Ashar Javed has uncovered a reflected XSS (Cross-Site Scripting) flaw in Google's most recent product, YouTube Gaming.
YouTube Gaming, Google's very own Twitch clone, works as a separate section of the famous YouTube video sharing portal, where online gamers can stream their games, watch other people play live, or view game-related clips.
The site was launched in August, and despite criticism and blowback from the competition, it eventually made a market niche for itself.
Mr. Javed, a security researcher that has been quite active in the past few years, previously managed to uncover various security bugs in products from Microsoft, Google, Yahoo, Twitter, eBay, Adobe, Etsy, AT&T, and Facebook.
Driven by curiosity about Google's newest service, Mr. Javed went on a quick tour of the website, and as he claims, after two minutes on the site, he managed to find a quite basic XSS bug.
Google did a decent job protecting the site, but not good enough
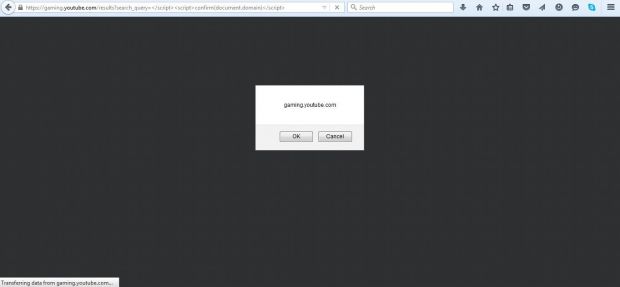
According to a quite technical blog post Javed published on Blogspot, while Google's security team took some steps to prevent the service from being vulnerable to XSS attack vectors, the team slipped up when it came to escaping a few trigger characters.
Javed says that Google's devs did their work and escaped or converted dangerous characters like ", ' and <, so attackers won't be able to use them.
The problem is that the < / combo is not protected, and this allowed the researcher to use a simple exploit in the form of:
Mr. Javed claims he reported this very same vulnerability to other sites in the past, including Netflix, Yandex, and ten other top sites that he declined to name.
For his efforts in helping Google fix this problem on YouTube Gaming's site, Mr. Javed was awarded a bug bounty of $3,133.7 / €2,847.
$3133.7 :D #Google #VRP pic.twitter.com/ZtrAwufaVm
— Ashar Javed (@soaj1664ashar) October 29, 2015
 14 DAY TRIAL //
14 DAY TRIAL //