The iSpy keylogger was updated to version 3.x two weeks ago, and it didn't take long for its recent version to pop up on the radar of cyber-security companies.
iSpy is currently advertised on a notorious underground hacking forum, where the crook is making his malware available under several monthly subscription plans.
iSpy has been quite a popular tool among crooks when it comes to keyloggers, with a previous campaign detected by Proofpoint in May.
At the time of writing, the iSpy homepage is down, but some sales must have happened because security researchers from Zscaler have reported infections with this most recent version.
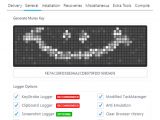
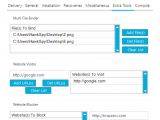
iSpy comes with a builder and backend control panel
As far as its features go, with a little bit of effort, the man behind this malware, a malware developer named CorelMASTERX, could very easily transform it into a full-blown RAT.
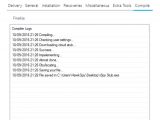
Currently, based on Zscaler's analysis and the forum ad Softpedia has seen, the trojan includes some of the standard features you'll find in most top-shelf malware offerings sold online these days.
For starters, iSpy comes with the obligatory builder which lets buyers compile their own version of the malware, with only the data theft features they need in order to keep the payload's size down as much as possible.
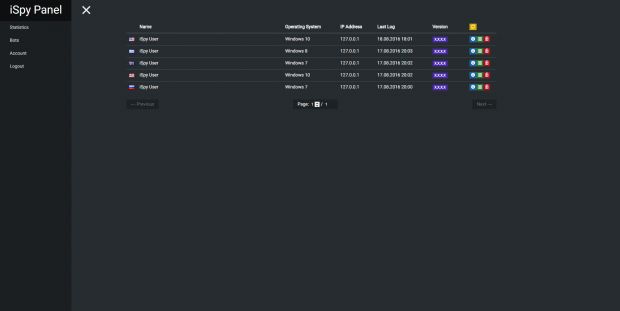
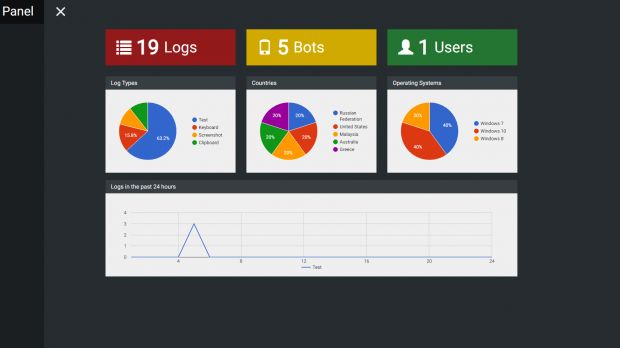
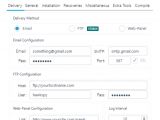
Secondly, a self-installable backend panel is also available, allowing crooks to receive and view data from their victims, and issue new commands.
The keylogger contains the obvious keylogging functionality, but also other features such as the ability to steal clipboard data and dump passwords from various applications.
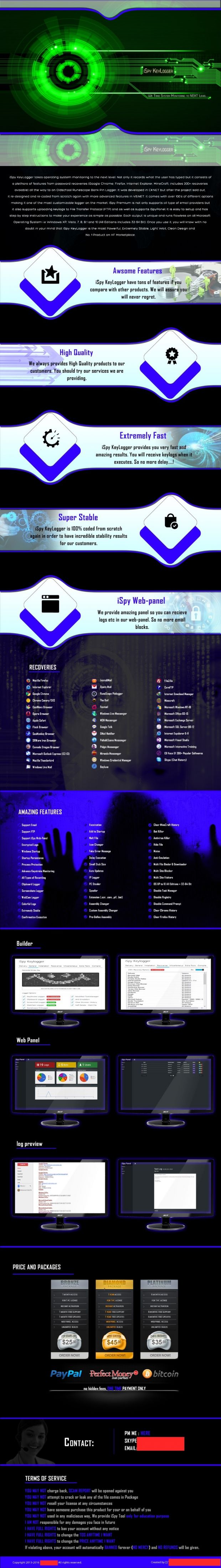
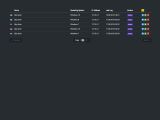
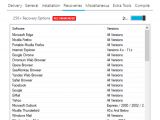
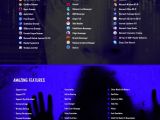
The password dumping feature, according to the infographic below, supports applications such as Firefox, Chrome, IE, Safari, Opera, Outlook, Thunderbird, Windows Live Mail, Filezilla, CoreFTP, Pidgin, and PalTalk, just to name the most important ones.
Besides dumping passwords, there was a function to recover software license keys for applications such as Windows, Microsoft Office, SQL Server, Microsoft Visual Studio, Minecraft, and others.
Additionally, there are features included to steal RuneEscape store PINs, and also dump Skype's chat history.
iSpy provides top-notch protection from antiviruses
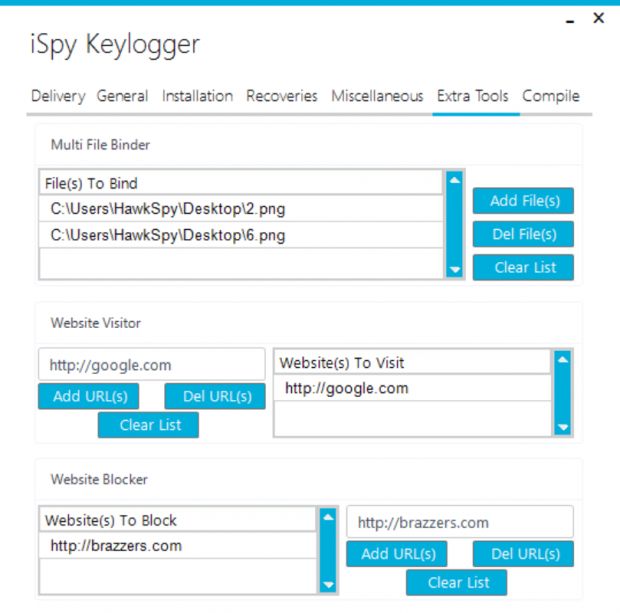
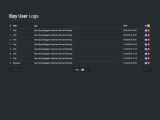
Other iSpy features allow users to block access to specific websites using the local host files, disable access to Windows features (cmd.exe, Task Manager, Regedit, etc.), and take screenshots of the user's screen or via the webcam.
To avoid detection by antivirus software, when the keylogger gains persistence via its own registry key, it also adds another registry key designed to prevent antivirus software from starting.
Similarly to most malware these days, the iSpy source code is protected using several custom packers, and the payload signed by a digital certificate, most likely forged or stolen.
Furthermore, several anti-VM and anti-analysis tricks are included in the source code to make reverse analysis by security researchers much more challenging.
iSpy can make the leak to a RAT if the author wishes it
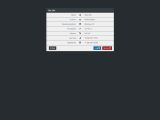
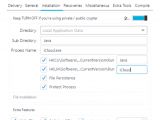
Once the iSpy malware finds and collects the information it was meant to gather, it can exfiltrate the stolen data to an email address, to an FTP server, or by uploading it via HTTP to an online server.
More interesting is that iSpy also includes a file downloading utility. If the crook manages to add support for more OS-level interaction features, this could be a capable RAT by the end of the year.
But don't consider iSpy an original piece of malware just yet. According to MalwareHunterTeam, this is just another piece of software copy-pasted from different other malware families.
Recent malware campaigns that have spread iSpy were email spam floods that delivered malicious JavaScript files or Office documents that installed the keylogger as a second-stage download. Users who avoid opening unsolicited email should be safe from this threat.
Just like most keyloggers and RATs, iSpy is most likely used to gain access to corporate computers, from where stolen data can be easily monetized on the Dark Web.
PS: Somewhere in the infographic below you'll see CorelMASTERX claim that iSpy is "only for educational purposes." It's not. This is malware 100%. In recent years, many malware authors are taking the high road and say they're developing software for the greater good, but when they advertise this tool on underground hacking forums, they reveal their real intentions.
 14 DAY TRIAL //
14 DAY TRIAL //