Banks, telcos, and even governmental agencies in the United States, South America, Europe, and Africa are being targeted by hackers in a series of ongoing attacks that are extremely difficult to detect.
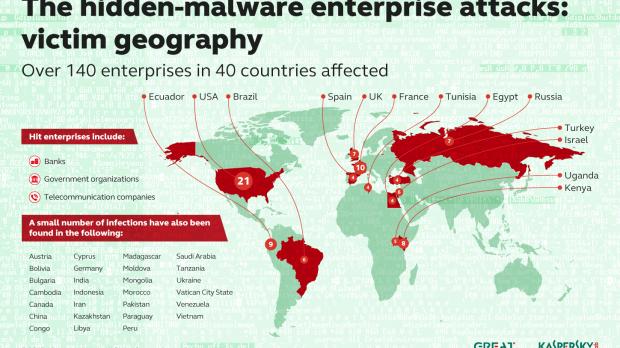
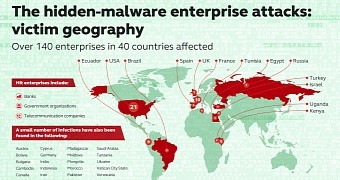
According to a new Kaspersky Lab report, at least 140 banks and other enterprises have been infected by malware that’s nearly invisible. Although this is the official number as of right now, given the difficulties involved in spotting this malware, the number could be much, much higher, Kaspersky specialists warn.
This is the same type of infection that Kaspersky found on its own corporate network a couple of years ago, an infection unlike anything they’d seen before. Duqu 2.0, as it was dubbed, was believed to be derived from Stuxnet, the sophisticated computer worm that was supposedly created by the US in collaboration with Israel to sabotage the nuclear program in Iran. Duqu 2.0 managed to remain undetected on Kaspersky’s network for at least six months.
New attacks
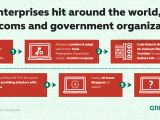
Now, a similar infection is spreading like wildfire among countless companies, including many banks. These hard-to-detect infections use legitimate system admin and security tools, such as PowerShell, Metasploit, and Mimikatz to inject malware into computer memory.
Kaspersky has chosen not to name the institutions that are currently under attack for obvious reasons, but they did mention that they come from 40 different countries. The United States, France, Ecuador, Kenya and the United Kingdom are the five most affected nations.
What makes these series of attacks particularly nasty is the fact that on top of being nearly impossible to detect for long periods of time, it is unknown just who could be behind it all - whether there’s a single group of individuals or numerous hacker groups. Unless someone claims the attacks, there’s going to be a long wait before the security researchers and authorities figure out just who’s responsible.
How does it work?
The first discovery of this particular malware took place in late 2016. Then, a bank’s security team found a copy of Meterpreter on the physical memory of a Microsoft, domain controller. The forensic analysis revealed that the Meterpreter code was downloaded and injected into memory with the help of PowerShell commands.
The Microsoft NETSH networking tool was also used by the infected machine to transport data to servers controlled by the attacker. Mimikatz was used by the attackers to obtain admin privileges necessary for such actions. To clean up the logs a bit, the PowerShell commands were hidden in the Windows registry, thus making it all difficult to track.
It seems that the method was used to collect passwords of system administrators and for the remote administration of infected host machines.
While the number of attacks is quite large, this seems to be the method used across most of them, which helped identify the extent of the situation.
 14 DAY TRIAL //
14 DAY TRIAL //