SecureWorks reports on a new tactic used by threat actors, who are now attempting to install and run a virtual machine, with the purpose of hiding their malicious actions.
For the non-connoisseur, virtual machines are emulated file systems, most of the times complete with a fully-running operating system that runs inside your existing operating system. In layman's terms is an OS inside your OS, allowing users to start Linux or Windows 98 just by clicking an icon on their desktop.
Virtual machines are generally used by software developers to test products and are often embedded in other applications, such as some security software.
Threat actor tried to install a new VM called "New Virtual Machine"
SecureWorks reports about a recent incident with one of their clients where their security platform detected some strange events on July 28, 2016.
After requesting more logs to analyze from the affected company's sysadmin, the researchers discovered the log lines that made their product trigger the alert.
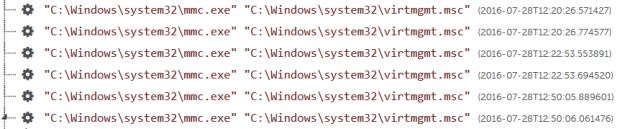
"The adversary had achieved a level of access that allowed them to interact with the Windows Explorer shell via the Terminal Services Client," SecureWorks Counter Threat Unit (CTU) researchers noted.
"Figure 1 shows the threat actor using the Microsoft Management Console (MMC) to launch the Hyper-V Manager, which is used to manage Microsoft's virtual machine (VM) infrastructure," the team added.
VMs can hide malicious actions from security products
The intruder tried to start a virtual machine on the infected host. Fortunately for the compromised company, the machine the intruder managed to gain access was a virtual machine itself, and virtual machines can't be nested inside each other.
The attacker failed in his attempt, but this shows a new tactic threat actors are now using to hide their activity on hacked systems.
Their plan is very smart and well thought through, because after setting up and launching a virtual machine, they would have been able to connect to the VM, and execute malicious actions, like exfiltrating sensitive data, out of the reach of security products.

 14 DAY TRIAL //
14 DAY TRIAL //