A new malware is infecting IoT devices, which in theory is not actually a piece of malware because it's not doing anything bad to the infected devices, but on the contrary, it is protecting them from further infections.
This Batman of malware families was detected by Symantec under the name Linux.Wifatch, and it specifically targets WiFi routers, IP cameras, surveillance systems, and other Internet-connected devices.
The infection occurs with Wifatch brute-forcing its way through easy-to-guess and default Telnet credentials, and then, instead of exfiltrating data or adding the device to a DDoS botnet, the malware starts cleaning up the device and setting up basic protection measures.
Symantec hasn't seen any type of malicious activity being carried out with Wifatch since it first saw it in action back in 2014, but it is not ruling out future suspicious activity either.
Wifatch behaves more like an antivirus rather than a virus
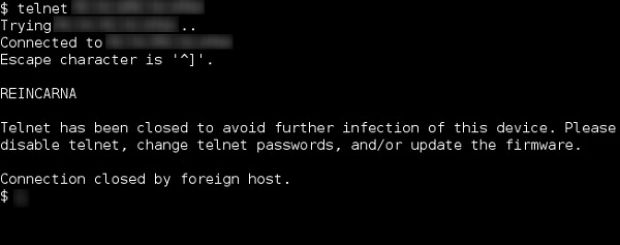
Currently, after infecting IoT devices, Wifatch starts performing a series of good-will gestures like shutting down Telnet access, updating the firmware, and sometimes leaving a message in the admin console, asking the device's legitimate owner to change their password to a more secure one.
Additionally, the malware also removes other well-known malware families if it finds them on the device, and in the case it infects the Dahua DVR CCTV systems, it also starts a custom module which restarts the CCTV system every week. This procedure is carried out to remove any malware that might infect the system, a reboot being more than enough to clean out the device's memory of such threats.
Linux.Wifatch is written in Perl, and as Symantec's researchers point out, its source code is not protected from reverse-engineering at all. The malware's creator even left a message in the source code, in the form of a quote from Richard Stallman, a famous software freedom activist. The message goes as follows:
"To any NSA and FBI agents reading my email: please consider whether defending the US Constitution against all enemies, foreign or domestic, requires you to follow Snowden's example."
The Wifatch malware can still be weaponized at any moment
While this seems the work of a vigilante trying to protect devices exposed to malicious attacks, let's not rule out the possibility that it might be an alpha or beta version of a much stronger malware family, currently going through a testing phase.
Its owner can easily weaponize Wifatch at any time, as Symantec says it has found backdoors in the malware's code, protected with cryptographic signatures.
The backdoor would allow the malware owner to send instructions to the malware at any time, make it download new modules, other malware payloads, all while the cryptographic signatures protect its code from being hijacked by other attackers.
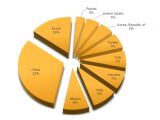
For now, Wifatch has been infecting IoT devices running on ARM architectures, and has been seen in China, Brazil, Mexico, India, Vietnam, Italy, and Turkey.

 14 DAY TRIAL //
14 DAY TRIAL //