Microsoft's developers spent most of their time in 2015 closing security bugs in Internet Explorer and UMC (User Mode Components), as ESET's Windows Exploitation in 2015 report reveals.
Microsoft's security bugs grew in numbers overall, going up to 571 in 2015 from 2014's total of 376, as aggregated data from CVE Details reveals.
The ESET report highlights that, out of all these bugs, 12 were zero-days, meaning they were actively exploited in the wild before Microsoft got to patch them. Four of these zero-days were found in Internet Explorer, three in the Windows UMC, four in Win32k (kernel component of the Windows GUI), and one in KM (Kernel Mode) drivers.
Security bugs in Windows UMC quadrupled
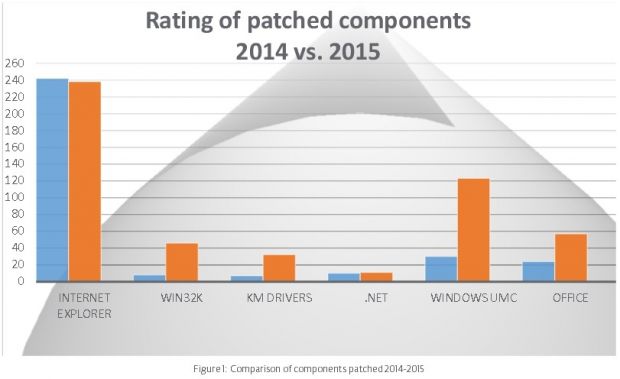
In total, Microsoft fixed most security bugs in Internet Explorer (~240), Windows UMC (~120), Office (~60), Wind32k (~40), KM drivers (~30), and the .NET Framework (~10). While bugs in Internet Explorer were slightly down from 2014, security bugs for UMC grew four times.
ESET also reports that most of these patches were intended to fix RCE (Remote Code Execution) and LPE (Local Privilege Escalation) issues. Microsoft's staff patched the most RCE issues in Windows UMC and Office while most LPE bugs were fixed in Windows UMC and the KM drivers.
For Internet Explorer and Edge, most of the bugs addressed issues that allowed attackers to carry out drive-by download attacks, which makes sense since browsers are most of the time the entry point for malware, which goes on to target RCE and LPE flaws in other applications.
The combination of drive-by downloads and an LPE was often used in 2015 by malware operators, with ESET reporting that most of the time they used these Windows exploits together with vulnerabilities in Adobe Flash (CVE-2015-0310, CVE-2015-0311, CVE-2015-0313, CVE-2015-3113, CVE-2015-5119, CVE-2015-5122, CVE-2015-5123) and Firefox's PDF viewer (CVE-2015-4495).
Security-wise, Edge is a step forward when compared to IE
A big role in putting Windows users at risk was also played by the Hacking Team data breach, which unleashed a large number of zero-days in the wild and kept Microsoft's security staff working around the clock to fix their own issues, but also coordinate security patches with Adobe.
The best thing that comes out of ESET's review of Microsoft's 2015 security patching activity is Edge, which the antivirus vendor lauds as being a step forward when compared to IE.
For starters, the browser does not support a bunch of Microsoft's older technologies that left wide gaping holes in IE's defense. Secondly, Edge also features top-of-the-line security features like protection against binary injection attacks, which have always been a problem, even for antivirus makers, let alone a meager browser like Edge, which can't even run extensions yet.
Overall, Microsoft has been much more active in fixing security issues, but these numbers are about to go down this year, as the company has recently dropped support for IE 8, 9, and 10, which means the IE crew will be less busy this year since they'll only cater to IE 11.

 14 DAY TRIAL //
14 DAY TRIAL //