Intel Security has patched a critical vulnerability in the Enterprise Security Manager, part of the McAfee line of security products.
The McAfee Enterprise Security Manager (codenamed SIEM ESM) is a powerful threat detection and analysis system developed by McAfee, prior to being acquired by Intel and the company being rebranded into Intel Security.
SIEM ESM is commonly found in larger enterprises, helping sysadmins protect their networks against a wide range of attack types.
Attackers can log in as admins without the correct password
According to research carried out by QuantumLeap, the McAfee Enterprise Security Manager is vulnerable to a simple-to-exploit authentication bypass vulnerability.
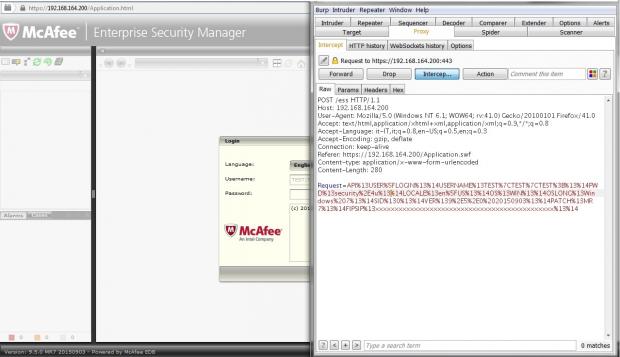
Security researchers say that using an incredibly simple username, attackers can have access to an admin-level account, without entering the correct password. The user in question is "NGCP|NGCP|NGCP" and can be used for SIEM ESM versions 9.3.0 and up to 9.5.0MR7.
Any password the attacker types in the login field should work, and only SIEM ESM installations configured to use Active Directory or LDAP authentication sources are vulnerable.
Intel Security has addressed the vulnerability by releasing SIEM ESM versions 9.5.0MR8 or 9.4.2MR9. Other products like Enterprise Security Manager/Log Manager (ESMLM) and Enterprise Security Manager/Receiver (ESMREC) were also vulnerable to this issue, and were also patched.
The vulnerability is easy to exploit, but SIEM ESM is hard to reach
This security issue, also detailed in CVE-2015-8024, has a base vulnerability severity score (CVSS-v3) of 9.8 out of 10, mainly due to the easiness with which an assailant can carry out attacks.
Since version 9.3.0 has been released in 2013, the vulnerability was around for more than two years before QuantumLeap researchers noticed its presence.
The only thing that might have protected companies during the past years was the fact that most SIEM ESM installations are usually placed inside Intranets and protected by strong firewalls. Nevertheless, infected computers on an Intranet can provide a way to authenticate on SIEM ESM and then disable its security shields.
Softpedia has contacted Intel Security for more details regarding the issue and we'll update the article as soon as we hear back.
 14 DAY TRIAL //
14 DAY TRIAL //