SQL injections are the ugly step-brother of DDOS attacks, maybe not as glamorous but many times more effective.
Unlike DDOS attacks, which can be carried out regardless of the client's server architecture, SQL injection attacks rely on the presence of a flaw in the target's software, or the use of bad coding practices.
SQL injections usually end up granting an attacker read access to a database, exposing information, or even worse, giving them write access or full control over the data, which can later be held for ransom.
In the past, companies like Yahoo!, Bell Canada, Kaspersky Lab, The Pirate Bay, the MySQL website, Barracuda Networks and many smaller government services and universities have fallen victim to this kind of attacks.
The results of an SQL injection are always both a technical and PR nightmare, involving an overhaul of the company's entire data storage layer, along with the fallout that comes with dealing with the media and the angry end users (if any).
The infographic below was created by Jack Leonard from Barricade, an Irish company focusing on security products for small to medium businesses.
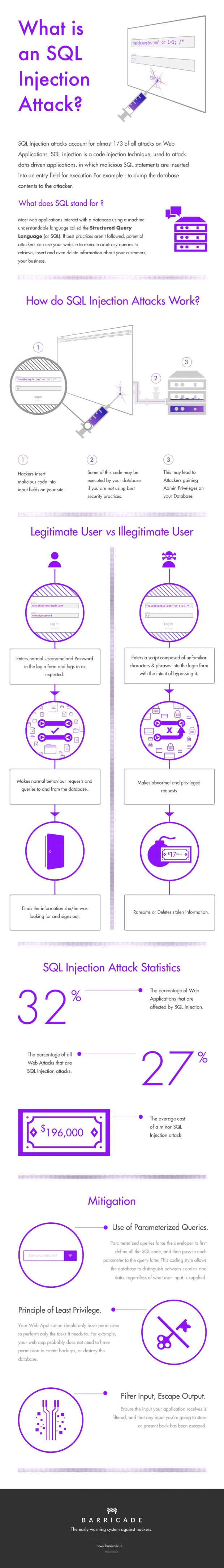
It presents the basic steps an SQL injection attack goes through, and it also shows some statistics, an aggregation of industry stats, and Barricade's own data.
As you can see from the data, 27% of all Web attacks are SQL injections, which doesn't surprise us since hackers can obtain solid data they can sell on the Dark Web, instead of boasting to their friends "Hey I DDOSed someone today!"
 14 DAY TRIAL //
14 DAY TRIAL //