CSRF attacks are probably the hardest attacks to understand, and also the most underestimated of all Web attack vectors present on the OWASP Top 10.
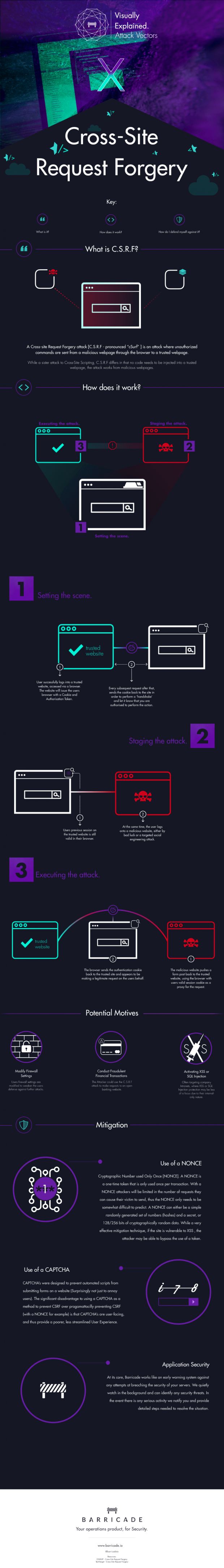
CSRF, or XSRF, stands for Cross-Site Request Forgery, and in the most simplistic explanation, it refers to when a malicious actor forces the user's browser to execute unwanted commands in the context of an application on which the user is authenticated.
The dangers of these types of attacks were understood by browser makers, who introduced anti-CSRF protection measures in their browsers in the form of an anti-CSRF token that gets added to a Web application's cookie file when the user logs in on a site.
Regardless of this, hackers have continued to discover new methods of using CSRF attacks, which can be quite damaging if chained together with other types of Web attacks, such as XSS and SQL injections.
An example of a CSRF attack is when the attacker gets ahold of the user's cookies via XSS, and uses them to transfer money out of the victim's bank account.
To defend against CSRF attacks, developers can deploy CAPTCHAs with their forms, use multi-step transactions, or harden their anti-CSRF tokens with cryptographic nonces (numbers used only once).
If you like the infographic below, there are others you can check out, about XSS, SQL injections, and DDoS attacks. All were made by the talented people at Barricade, a cyber-security vendor providing cloud security systems.
 14 DAY TRIAL //
14 DAY TRIAL //