A weak design in the passbooks of several Indian banks can be leveraged to obtain a client's account balance and his transaction history.
This flaw was discovered by Indrajeet Bhuyan, an independent security researcher that previously identified two WhatsApp vulnerabilities we reported about in December 2014 and January 2015.
His most research started after the State Bank of India introduced automatic passbook printers in his country, with other banks soon following suit with their own machines.
If you haven't ever saw a passbook, it's a small card which bank tellers and automatic passbook printers would use to print out the client's current account balance and his most recent transactions.
They have become obsolete with the rise of online and mobile banking, but in some parts of the world where Internet connections and mobile networks are scarce or too expensive, they are still used successfully.
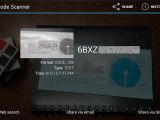
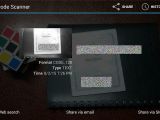
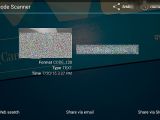
According to Mr. Bhuyan's research, banks in India use a simple barcode printed on the passbook, as the sole method of authentication with their automatic passbook printing stands.
The vulnerability resides with automatic passbook printing stands
Since no other authentication or encoding system is used, an attacker could easily spoof a passbook barcode and obtain the account history and balance for other customers.
All what's left to do is to find out the target's barcode, or in this case, his account number, which in all corners of the world is considered personal (not public, nor private) information.
While this can be a little tricky, investigating the practices of three banks, Mr. Bhuyan discovered that two of them use the customer's bank account number as the barcode's data.
These banks are UCO Bank and Canara Bank, while the State Bank of India used different IDs for the passbook and the account number.
Since all banks used Code 128 as the method of encoding the barcode, a very well known standard, Mr. Bhuyan carried out two tests to verify his theories.
In the first case, he altered his father's passbook, by removing the bank barcode applied as a sticker, and pasted his own barcode created by converting his father's bank account into a Code 128 barcode.
In the second test, he took his father's passbook and using the same method, he applied another custom generated barcode obtained by encoding his own bank account number using Code 128.
The passbooks don't use any authorization outside the Code 128 barcodes
Both cases proved successful, and the automatic passbook printers plotted personal and private information to the passbook card after reading Mr. Bhuyan's home-made barcodes.
No biometric authentication, no passwords, no encryption! All was done without proper authentication, putting a client's private financial information into the hands of any person curious enough to go searching for it.
IT departments of several banks were informed of the issue, but none has replied to Mr. Bhuyan, even after a week. You can read a more in-depth report of the whole research on Mr. Bhuyan's blog.

 14 DAY TRIAL //
14 DAY TRIAL //