The IBM X-Force Threat Intelligence Quarterly report is out and its results point to an increase of malicious traffic originating from Tor exit nodes.
Aggregating data from IBM's Managed Security Services from January 1 to May 10, the IBM researchers highlight an increase not only in the number of TOR exit nodes but also in the malicious traffic that's being funneled through them.
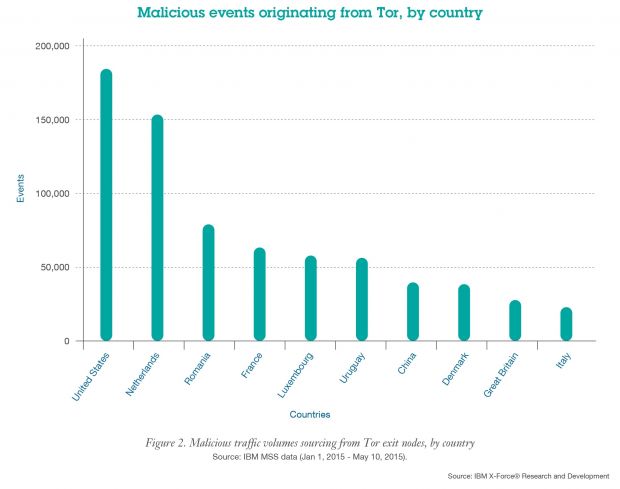
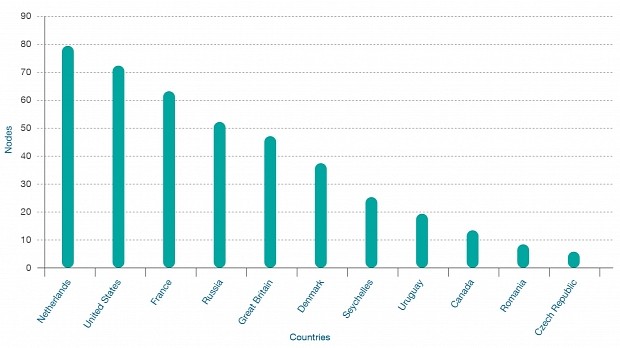
While Holland, the US, France, Russia and the UK host the most Tor exit nodes, most malicious traffic seems to be coming out of nodes hosted in the US, Holland, Romania, France, and Luxembourg.
The recorded attacks that hide their source using Tor seem to be targeting the Information and Communications sector primarily, followed by Manufacturing, Finances and Insurance, Education, and Retail and Wholesale industries.
Attackers use Tor for hiding SQL injections and vulnerability scanning
When it comes to what kind of attacks malicious parties carry out via Tor, the most common ones are SQL injections, something that surprised IBM security researchers, who said that "After all these years, the world continues to create websites vulnerable to SQLi."
If IBM hadn’t been a tightly controlled corporation that closely watches its press releases, this would have been the perfect place to insert a SMH (Shaking My Head) GIF.
Second on the list of favorite attacks to be carried out via Tor is vulnerability scanning attacks, followed by the famous DDOS floods.
While vulnerability scanning is currently easily detectable by most enterprise-level firewalls, Tor offers a way for attackers to not only hide their real location but also quickly change their exit node when its IP is detected and banned.
As for DDOS attacks, Tor exit nodes in the US seem to be the favorite ones for many attackers, mainly because they offer bigger bandwidths compared to other nodes around the globe.
The IBM report ends with a warning that says, "Expect use of these services [Tor exit nodes] in attacks to expand and to make them somewhat harder to unravel [...] Corporate networks really have little choice but to block communications to these stealthy networks."
 14 DAY TRIAL //
14 DAY TRIAL //