Security researchers from FireEye have discovered that, despite Apple’s attempts to secure iOS 7 and iOS 6 last week, there is still a serious vulnerability inside the software that can allow a hacker to perform keylogging attacks.
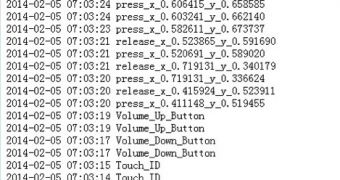
FireEye writes on its blog, “We have created a proof-of-concept ‘monitoring’ app on non-jailbroken iOS 7.0.x devices. This ‘monitoring’ app can record all the user touch/press events in the background...”
These events include screen touches, home button presses, and even volume button presses. The TouchID fingerprint sensor is no exception, “and then this app can send all user events to any remote server.”
“Potential attackers can use such information to reconstruct every character the victim inputs,” the security researchers say.
The security firm explains that the “background app refresh” feature in iOS 7 disables unnecessary refreshing and “contributes to preventing the potential background monitoring,” but adds that “it can be bypassed.”
The blog post includes an example using the music app that plays in the background without having to turn on its “background app refresh” behavior, since it’s designed differently for multitasking.
As such, FireEye says, “a malicious app can disguise itself as a music app to conduct background monitoring.”
The firm asks readers to note that the flaw affects all device models and all iOS versions up to the latest firmware updates dished out by Apple last week.
“Note that the demo exploits the latest 7.0.4 version of iOS system on a non-jailbroken iPhone 5s device successfully. We have verified that the same vulnerability also exists in iOS versions 7.0.5, 7.0.6 and 6.1.x,” FireEye writes.
It then warns that customers are susceptible to remote attacks, meaning Apple will have to deliver yet another firmware patch in the near future.
“Based on the findings, potential attackers can either use phishing to mislead the victim to install a malicious/vulnerable app or exploit another remote vulnerability of some app, and then conduct background monitoring.”
An earlier post from FireEye, which got removed for one reason or another, said (emphasis ours), “FireEye successfully delivered a proof-of-concept monitoring app through the App Store that records user activity and sends it to a remote server. We have been collaborating with Apple on this issue.”
In other words, expect this flaw to get patched either in iOS 7.0.7 or iOS 7.1, a forthcoming update known to be in development at Apple.
The Cupertino giant still has to patch a widely reported SSL/TSL flaw in its OS X Mavericks operating system.
 14 DAY TRIAL //
14 DAY TRIAL //