Apple ID credentials are all a hacker needs to gain access to a victim’s content in Apple’s cloud storage, as two-factor authentication (2FA) is not required for restoring iCloud backups.
The feature is designed to confirm the identity of the account owner through a code sent to a physical device, after the username and password have been entered.
As per Apple’s support page, 2FA is used for signing into the My Apple ID, for an iTunes, App Store, or iBooks Store purchase from a new device and for getting Apple ID related support from the company.
Other actions requiring authentication do not resort to the two-step protection feature, and these include installation of iCloud backups on new devices; this operation only needs the username and password for the account.
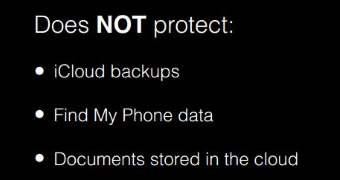
Vladimir Katalov from ElcomSoft held a presentation in November 2013 at the DeepSec conference in Vienna, about how Apple iCloud works, where he said that Apple’s 2FA did not affect iCloud backups, Find My iPhone data or documents stored in the cloud.
The information stored on the company’s servers benefits from other forms of protection, such as encryption, with the keys being held by Apple.
The researcher said that no notification was sent to the owner of the account after downloading a backup, as would occur in the case of the restoration procedure.
Given this information, despite the advisory from the California-based tech giant to enable the two-step verification feature for protecting access to the iCloud account, hackers could extract data users stored in the cloud, provided the username and password were known; and no system breach would occur.
Photo Stream is also accessible without having to input the third verification code after logging in.
The new information sheds some new light on the methods possibly used by the hackers to break into the accounts of more than 100 female celebrities and extract compromising images with them in the nude.
Up until recently, unauthorized access to iCloud could have been gained by simply brute-forcing the login feature. Obtaining the victim’s username is not too difficult for a hacker with social engineering skills or ready to engage in a thorough search of the public information available online.
The next step for Apple in order to strengthen the protection of customer private data is probably to extend 2FA to all iCloud services. Users have already started to lose their trust in the much touted impenetrable defenses of Apple products though.
 14 DAY TRIAL //
14 DAY TRIAL //