Fabian Wosar, Emsisoft security researcher at day and ransomware killer at night, has made two new victims after releasing a new decrypter for the HydraCrypt and UmbreCrypt ransomware families.
Both ransomware families are new and were initially detected this year, first HydraCrypt and then UmbreCrypt. At their core, both stem from the CrypBoss ransomware variant that somebody leaked last year, putting its source code on PasteBin.
With its source code out in the open, security researchers quickly cracked its encryption algorithm and provided decrypters for the original variant and all of the subsequent mutations that evolved from the PasteBin leak.
Despite encryption error, both ransomware families can be cracked
As more data gathered on these two new families, Mr. Wosar was eventually able to adjust his previous CrypBoss decrypter to target these two new threats.
"Unfortunately the changes made by the HydraCrypt and UmbreCrypt authors cause up to 15 bytes at the end of the file to be damaged irrecoverably," the researcher explained.
The good news is that, most of the times, these bytes are useless, being usually added as buffer data, and don't always affect the decryption process. Additionally, the people behind these two new ransomware variants made very few modifications to the original CrypBoss source, so their ransomware's encryption algorithm is still vulnerable.
Mr. Wosar's decrypter, which is available for download via Emsisoft's site, will be able to tackle both HydraCrypt and UmbreCrypt at the same time.
How to crack the encryption key and how to decrypt files
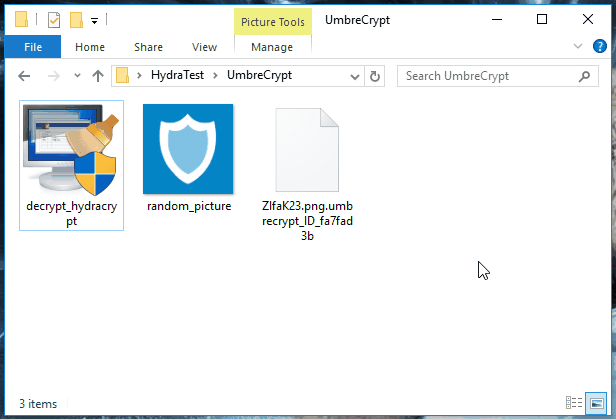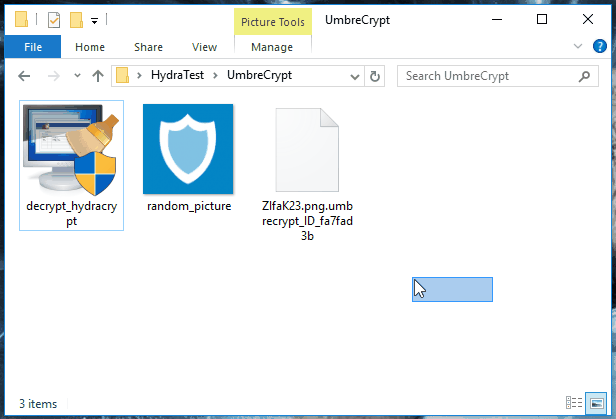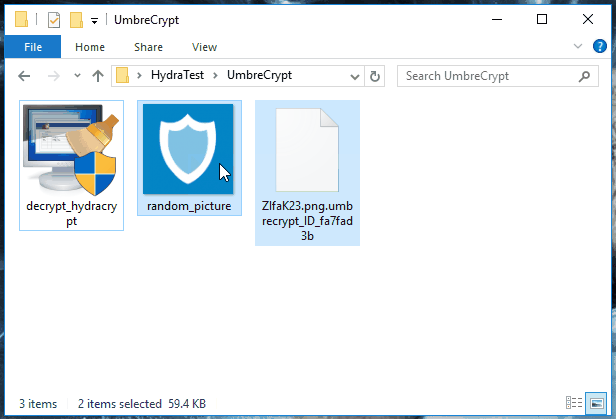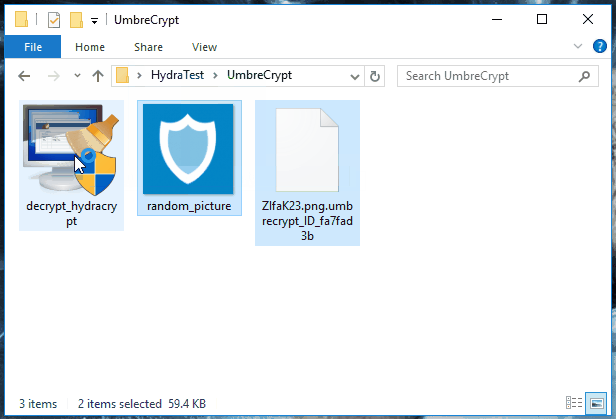
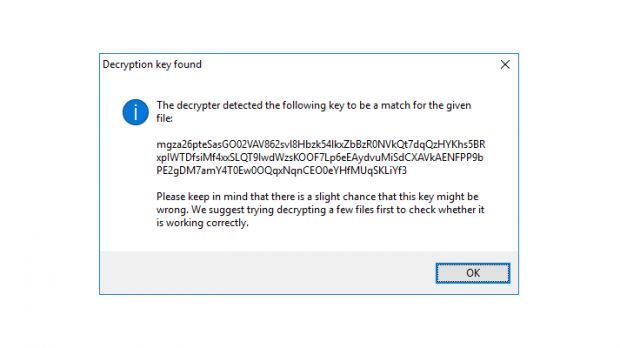
To decrypt their files, users should first extract the decryption key. They can do this by taking an encrypted file along with its original version (if available from a backup location like Google Drive, Dropbox, email, portable hard drive). The user should select both files and drag-and-drop them over the decrypter's executable. See animated GIF below.
If they can't find a file in both encrypted-original format, users can also get a random encrypted file and a random PNG image off the Internet, and also drag-and-drop it over the decrypter's executable.
This gesture will start the encryption key cracking process, which may sometimes take a day or longer. Once the decryption key is obtained, users should write it down on paper just to be safe and then copy-paste it inside a text file for later use.
Once you have the decryption key in hand, you can double-click the decrypter to start it outright, select the folders you want to decrypt files from, enter the decryption key, and sit back for the next day or so until all files are cracked.
Mr. Wosar suggests testing the decryption key first on one single file to be sure it works correctly. Additionally, the decrypter does not delete the encrypted files, so make sure you have enough space on your hard drive to store all the decrypted files.
 14 DAY TRIAL //
14 DAY TRIAL //