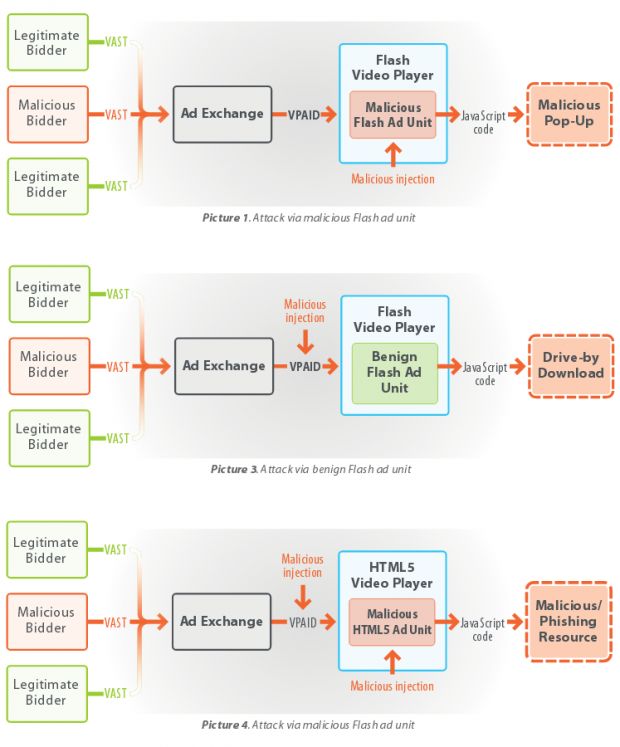
A study from GeoEdge, an ad scanning vendor, reveals that Flash has been wrongly accused of being the root cause of today's malvertising campaigns, but in reality, switching to HTML5 ads won't safeguard users from attacks because the vulnerabilities are in the ad platforms and advertising standards themselves.
The evidence exists to proclaim Flash as one of today's most vulnerable and insecure software applications. Targeted in cyber-espionage and malvertising campaigns, Flash has gotten a bad reputation, and for good reason.
HTML5 ads are replacing Flash ads in the industry
Security researchers have discovered vulnerabilities in Flash almost every month, and for many years, Adobe has been slow to patch them. Things changed recently after browser vendors threatened to have the plugin disabled for most of their users.
But Adobe's new approach to Flash security issues came a little too late, as the community had already worked for years on adding the appropriate features to HTML5 and other standards in order to replace Adobe's piece of junk.
HTML5 was officially released in October 2014, and slowly but surely, it started to replace Flash in the advertising market, where many ad networks such as Google and Amazon announced they'd stop taking static Flash ads, even if still allowing Flash for video ads.
Malvertisers don't care if ad is Flash or HTML5
According to the GeoEdge study, attacks using malicious ads, known as malvertising, do not necessarily rely on the underlying ad, but more on the insecure standards used to build the advertising network's infrastructure, regardless of whether they deliver static or video ads.
The company argues that, for video ads, the primary root of malvertising is the VAST and VPAID advertising standards. VAST and VPAID are the rules of the game when it comes to online video advertising, defining the road an ad needs to take from the ad's creator to the user's browser.
No matter if the ad is Flash or HTML5, there are critical points in this ad delivery path where ad creators can alter the ad via JavaScript injections. These same critical points are also there, so advertisers or ad networks can feed JavaScript code that fingerprints and tracks users.
If you want to blame a technology, blame JavaScript
A malicious ad creator can use their ability to send third-party JavaScript to the ad via AdParameter values. Instead of user tracking code or ad delivery instructions, they can very easily deliver malicious code instead. At no point does it matter to them if the ad was created in Flash or HTML5.
Of course, there's a discussion on whether HTML5 is actually an improvement over Flash. While Flash has better image quality rendering, HTML5 ads are usually larger in size. While Flash ads require a plugin to work, HTML5 ads don't work in older browsers. While Flash ads can be easily optimized, HTML5 ads are easier to create and work on mobile devices by default. In terms of security, HTML5 is the clear-cut winner, but currently, Flash ads are still a solid alternative.
"There are some advantages to Flash-based ads. However, in terms of security, HTML5 is the more secure option," says GeoEdge. "The main root of the video ad malvertising problem is, unfortunately, fundamental."
While GeoEdge's report only tackled video ads, the same thing goes for static ads, regardless of whether they're created in Flash or HTML5. The real problem is the design of some advertising networks that allow advertisers to deliver custom JavaScript. Be it an image, a Flash object, or anything else, the real exploitation point in malvertising attacks is not the ad, but the adjacent code.

 14 DAY TRIAL //
14 DAY TRIAL //