Hackers are becoming more and more innovative when it comes to finding ways to infect your computer. This time, you could get infected if you so much as hover your mouse over a link embedded in a malicious PowerPoint file.
According to security firm Trend Micro, this technique is employed by a Trojan downloader which has been uncovered in a recent spam email campaign in the EMEA region, particularly organizations across the United Kingdom, the Netherlands, Sweden, and Poland.
"The Trojan downloader we monitored and analyzed had a variant of OTLARD banking Trojan as payload (TROJ_ OTLARD.TY). OTLARD, also known as Gootkit, emerged as early as 2012 and soon evolved into an information-stealing Trojan with persistence, remote access, network traffic monitoring, and browser manipulation capabilities. In fact, OTLARD/Gootkit was used in a spam campaign in France last 2015, whose spammed messages masqueraded as a letter from the French Ministry of Justice," Trend Micro researchers state.
Gootkit is known for stealing credentials and bank account information from victims across Europe. Usually, its operators use malware-laced macros hidden in documents to deliver the payload, but this type is a completely new method.
Potential test run
This particular spam campaign reached a peak on May 25 with 1,444 detections, dropping to half the next day and dying down by May 29. This may very well have been a test run for the attackers, trying out the new technique.
Researchers are particularly worried about this new recipe being used for other types of malware, like ransomware.
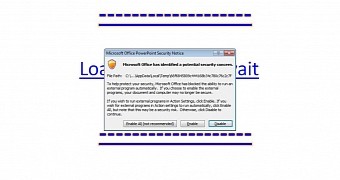
The malware starts as a spam email disguised as an invoice or purchase order. The message contains a malicious PowerPoint file, whether PPSX or PPS. Once the file is downloaded and opened, the victim isn't immediately infected. This only happens when they hover over the text or picture embedded with a malicious link. If you choose to enable the content to run when the security notice pops up, this will have you infected in no time.
Basically, it's the same social engineering that's required for those malicious macro documents too; if you say "yes" to those security prompts, you're allowing the infection without even fully realizing it.
"The trick will not work in Microsoft PowerPoint Online or Office 365’s 'web mode', as these don’t provide the actions functionality that is present in offline/desktop versions. An Office 365 end user, however, can still be affected if he accesses his account and opens the malicious file through a client (PowerPoint locally installed in the machine)," researchers point out.
The bottom line is to remember to always view documents in Protected View, especially with documents you have no real idea where they're coming from.
 14 DAY TRIAL //
14 DAY TRIAL //