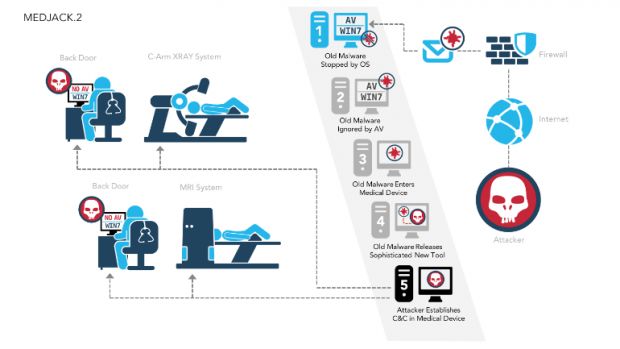
Medjack was first described in June of last year, when security firm TrapX explained an attack that relies on exploiting existing medical devices that run outdated software in order to enter the secure network of a healthcare unit.
The attacks were successful for a series of reasons. One of them was that, even if hospitals ran powerful security and scanning software, the attackers focused on older operating systems, such as XP, usually not supported by these security systems.
Secondly, attackers were successful because they targeted medical devices, and not the general IT network. At that point, attacking medical devices was still more of a theoretical scenario, and not something seen in the real world that much.
Things changed after TrapX's initial report, in which the company detailed a series of real-world attacks using the Medjack approach.
More Medjack attacks detected during the past year
In a new report released this week, the company is now detailing three more variations of the Medjack attacks observed in the real world.
The first was an attack against a well-defended hospital. Attackers hid their malicious code inside a Conficker worm, malware specialized to target older Windows XP versions and avoid newer OS releases.
The threat group managed to infect the XP machines used to control a fluoroscopic radiological system, a respiratory management system, and a radiation system used in the Oncology department.
Crooks left backdoors on these computers and came back to utilize them to move laterally in the hospital's network and compromise other systems.
Remediation can sometimes take weeks
In a second incident, attackers also targeted a well-protected healthcare unit, but this time, they aimed at its picture archiving and communication system (PACS).
Again, the attacker placed his malicious code inside the Conficker worm and infected the PACS system with a remote access trojan (RAT).
There was a complication around this attack because the PACS system hackers infected was an MRI system used in the hospital's Urgent Care unit, so it took the hospital weeks to remove the infection, during which time they had to cut the device's access to the Internet.
In the third attack, crooks used a similar tactic but targeted even older software. They wrapped malicious code inside a very old networm, which they used to infect a computer running Windows NT 4.0 attached to a C-Arm X-Ray system.
Medical records are extremely valuable on the black market
"The presence of medical devices on healthcare networks creates high vulnerability. These medical devices will make these networks much more susceptible to a successful cyber attack," TrapX writes in its report. "We noted this in early 2015, and now, in mid 2016 the tidal wave of medical device based attacks is prominent, visible, and trending substantially."
Why the increased focus on healthcare units? The answer is simple. It's because of the data's value.
For example, a hacker who goes by the name of TheDarkOverlord is selling healthcare records on the Dark Web and asking for half a million dollars for his database. Similarly, a hacker named Peace_of_mind, who's selling LinkedIn and MySpace account details, is only asking for a few hundred, even if he's selling ten times more user records.
Hackers tend to flock where the money is, and currently, they can get more by stealing and then selling medical records, so expect more attacks against the healthcare sector, and especially targeting its unsecured devices.

 14 DAY TRIAL //
14 DAY TRIAL //