It took a team of four French scientists to reverse-engineer a collection of stolen credit cards that were manually altered by attackers and used in an ingenious way to commit credit card fraud in France and Belgium.
The revelation comes via a recent research paper published by the École Normale Supérieure university in Paris, France, and the Science and Technology Institute (CEA), in which researchers document the work they did for French authorities, helping them investigate how a group of five French criminals managed to use stolen credit cards, despite the fact that the cards were protected by both a security chip and a PIN code, which the hackers did not know.
Hackers made fraudulent purchases of over $680,000
The five criminals were caught by Belgium authorities in 2012, after a French banking firm observed a spike in transactions coming from stolen credit cards, most of which originated from a few locations in Belgium.
Police eventually arrested a woman in one of the locations, and then four other men, responsible for creating the "hacked" credit cards.
The fraudsters managed to alter over 40 stolen credits cards, which they used to make over 7,000 fraudulent transactions, totaling more than $680,000 / €600,000.
Police asked the researchers to help during the investigation
Because police were not able to detect how the fraudsters used the fake credit cards, the researchers were brought in to help with the investigation.
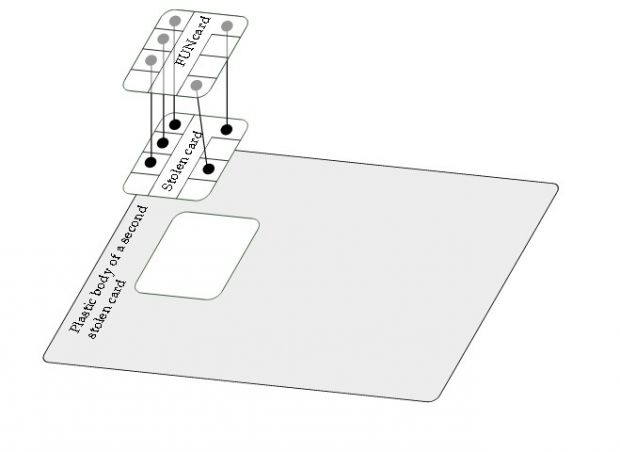
Acting on a hunch and based on research carried out by Cambridge University scientists, the French researchers suspected that the fraudsters managed to cram two different chips inside the stolen credit cards.
Analysis using X-Ray imagery and a closer look at the credit card chips' electrical activity proved they were right, and that the fraudsters managed to successfully implement the Cambridge method into a real-world attack.
According to their research paper, the French hackers bought FUNcard chips, and using glue, they managed to attach them on top of the original, stolen credit card chip.
When a transaction would be initiated, this dummy chip would interfere with the normal payment processing operation, but only when the PoS terminal would "ask" the credit card (original) chip if the entered PIN was correct.
The dummy chip would slip in between the PoS terminal and the original chip, and answer "Yes," allowing the transaction to go through.
This was a classic MitM (Man in the Middle) attack but carried out in a medium where you wouldn't normally guard against one.
Following their revelations, the fraudsters were eventually convicted and EMVCo, the consortium that regulates credit card payments, has put extra security measures in place so this attack would be harder to carry out.
"During our testimony we underlined to the court that this case shows that organised crime is following very attentively advances in information security," say the four French researchers. "It is important to underline that, as we write these lines, the attack described in this paper is not applicable anymore, thanks to the activation of a new authentication mode and network level protections acting as a second line of defense."
The full "When Organized Crime Applies Academic Results: A Forensic Analysis of an In-Card Listening Device" (PDF) research is available online.

 14 DAY TRIAL //
14 DAY TRIAL //