Two days ago, AVG security researcher Jakub Kroustek discovered a quite originally named ransomware variant dubbed the Hitler Ransomware (actually, Ransonware, but the grammar Nazi lying in me could not let that pass) that deletes your files as a result of bad coding.
The Hitler ransomware infection takes place when the user double-clicks on an infected binary. According to Bleeping Computer, this file drops a batch file on the user's system, which then drops three files, called firefox32.exe, ErOne.vbs, and chrst.exe.
Firefox32.exe is copied to the startup folder to ensure the ransomware starts with every PC boot. ErOne.vbs shows an error when the user clicks the original executable, making them believe the file contains an error. Chrst.exe is the actual ransomware, which displays the ransom note on the user's screen, starts the encryption process and a one-hour countdown timer.
The Hitler ransomware will encrypt the user's files and also delete their original extensions. When the countdown timer reaches zero, the chrst.exe file crashes spectacularly, causing a Windows BSOD (Blue Screen of Death).
When the computer recovers from the BSOD or the user restarts the PC, they'll find that Hitler (the ransomware) has deleted all the files in their User Profile folder.
Hitler ransomware created by a German-speaking developer
As Bleeping Computer's malware analyst Lawrence Abrams points out, based on the source code comments found in the batch file, the Hitler ransomware seems to be the work of a German-speaking developer.
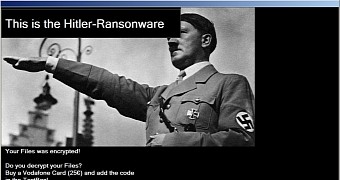
This idea is reinforced by the fact that Hitler asks for the ransom in Euros. In fact, the ransomware asks for the code of a €25 Vodafone telephony card.
"This ransomware appears to be a test variant," Abrams writes. "I hope this is not the actual code that this ransomware developer plans on using if it goes live."
Below we present a YouTube video showcasing the Hitler ransomware infection process, courtesy of Serbian security researcher GrujaRS.
 14 DAY TRIAL //
14 DAY TRIAL // 