Researchers have spotted a new ransomware family that attacks a hard drive's MBR (Master Boot Record) and prevents PCs from booting up after encrypting their files.
This one's named HDDCryptor (or Mamba) and has been around since January 2016, according to a Bleeping Computer forum topic where users reported their infections.
Technically, HDDCryptor was around before the overhyped Petya, and later Satana ransomware families, which got a lot more media attention, and behaved in the same way, by rewriting the MBR and preventing the PC from booting.
New wave of HDDCryptor infections
Based on available reports, it appears that a recent malware distribution campaign has been delivering a new version of HDDCryptor to users around the world.
The first one to (re)detect HDDCryptor was Renato Marinho, a security researcher for Morphus Labs, who said his company was called in to investigate a massive HDDCryptor infection at a multinational, which affected its headquarters in the US, Brazil, and India.
Marinho's initial technical analysis was followed a few days later by one from Trend Micro, mostly identical.
According to both, HDDCryptor infections start with users accessing a malicious website and downloading malware-laced files on their PCs. These files are either infected with HDDCryptor directly or come with an intermediary malware that delivers HDDCryptor at a later stage, when the crooks are sure they have boot persistence on the infected computer.
HDDCryptor uses open source tools to attack and lock PCs
The actual HDDCryptor payload is a bunch of binaries all crammed into one. When the big binary is executed, it drops files on the user's computer and launches them in a particular order.
HDDCryptor first scans the local network for network drives. It then uses a free tool called Network Password Recovery to search and dump credentials for network-shared folders, past or present.
The process continues by launching another open source tool called DiskCryptor to encrypt the user's files found on the hard drive's partitions. This tool is then used in conjunction with the previous scan and passwords to connect to network drives and encrypt that data as well.
Ransomware is efficient, some people have paid
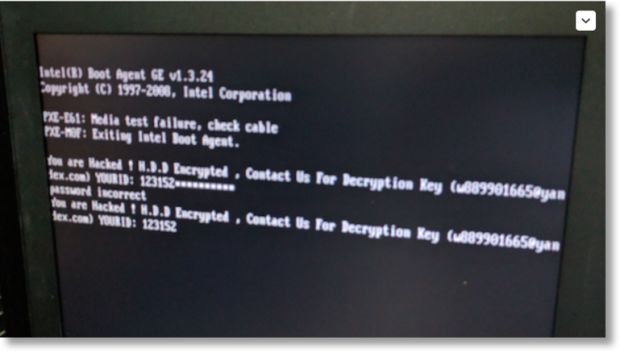
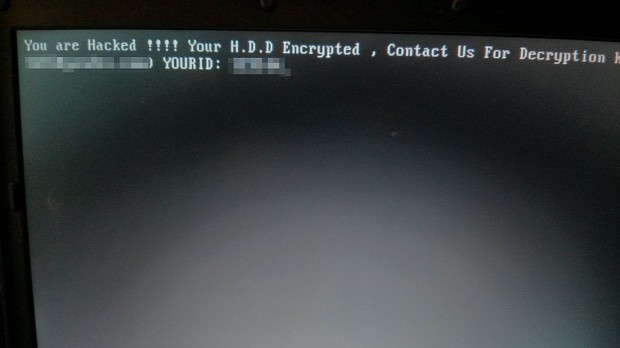
In the end, HDDCrypter rewrites the MBR with a custom boot loader and restarts the computer, which then gets stuck in a ransom note like the one below.
Users are encouraged to contact the ransomware's author via email, where they'll receive the Bitcoin address where to pay the ransom note. Crooks are currently asking for 1 Bitcoin (~$610).
According to funds found in one of the Bitcoin addresses shared in these emails, at least four people seem to have paid the ransom fee so far, but there are probably more if crooks used different Bitcoin addresses.
 14 DAY TRIAL //
14 DAY TRIAL //