Security researchers have discovered a new IoT worm that appears to share behavior with the more popular Mirai IoT malware, but which is far more sophisticated than the latter.
Because Mirai is the Japanese word for "future," they named this new variation Hajime, the Japanese word for "beginning."
Responsible for Hajime's discovery are Sam Edwards and Ioannis Profetis, security researchers for Rapidity Networks.
Researchers discovered Hajime while searching for Mirai
In a technical report on Hajime's activity released over the weekend, the two explain that they were drawn to investigate Mirai after they read that its author had released its source code online, for free. The two wanted to study both Mirai and how other hackers that now had access to its source code would end up using it.
To gather intel on the Mirai botnets expected to pop up after the source code's release, they set up honeypot servers all over the world.
On October 5, just three days after Mirai leaked online, the two discovered what appeared to be a Mirai infection, which at a closer look proved to be something new entirely.
This is how the two discovered Hajime, an IoT worm that spreads the same way as Mirai, but appears to be something new entirely, despite some shared behavior.
Hajime spreads on its own via brute-force attacks
Researchers say that Hajime uses a three-stage infection mechanism, and self-propagates. Stage 0 occurs on an already infected system, from where Hajime starts to scan random IPv4 addresses.
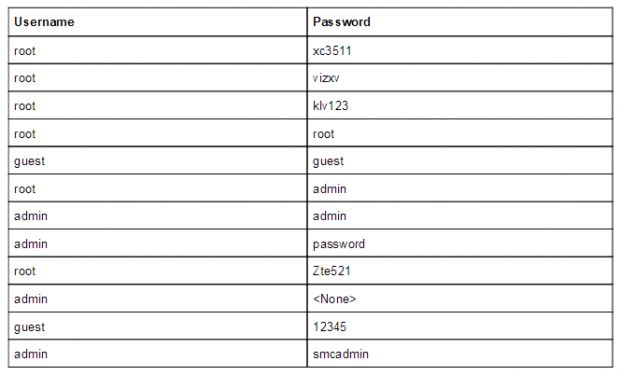
The worm launches a brute-force attack on port 23, trying to log in on the other end with a series of username and password combinations hardcoded in its source code. If the IP doesn't have port 23 open, or the brute-force attack fails, Hajime moves on to a new IP.
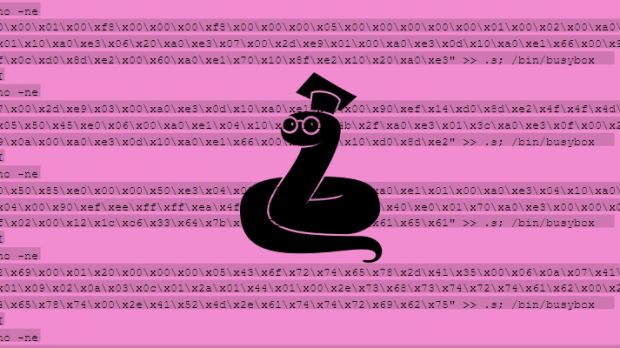
In the case of a successful connection, Hajime will execute the following four commands:
enable
system
shell
sh
/bin/busybox ECCHI
These will allow the worm to tell if it infected a Linux-based system. According to Rapidity researchers, Hajime can target the following platforms: ARMv5, ARMv7, Intel x86-64, MIPS, and little-endian.
Hajime uses a three-stage infection system
At this point, the worm enters Stage 1, and it starts the download of a foreign binary, a 484-byte ELF program. ELFs are Linux binary files, similar to EXEs on Windows.
The Hajime worm launches this binary, which has only one purpose, to open a connection to the attacker's server and write the bytes it receives to a new binary, launching it into execution when the data transfer finishes.
Researchers say this Stage 2 binary uses the DHT protocol to connect to a P2P botnet, from where it downloads further payloads (binaries, modules) via the uTP protocol. Both DHT and uTP are backbone protocols for BitTorrent clients.
Hajime is similar to many IoT malware families, but different
Hajime's mode of operation outdoes Mirai's and seems to have borrowed many tricks from other IoT malware as well.
Hajime uses DHT to connect to a P2P botnet, just like Rex; uses a list of built-in username & password combinations to brute-force random IPs and spread on its own, just like Mirai; and uses a multi-stage infection mechanism, just like NyaDrop.
The difference is that Hajime is written in C, not Go (Rex), uses a P2P network, not a direct C&C server connection (Mirai), and works with a larger number of platforms, not just MIPS (NyaDrop). So at this stage, Hajime seems to have included the best parts of other IoT malware, and it is far more sophisticated than anything else seen targeting IoT devices today.
Hajime targets IP cameras, DVRs and CCTV systems
Based on the hardcoded credentials included in the worm's source code, Hajime targets routers, DVRs, and CCTV systems, just like Mirai and NyaDrop.
More specifically, Hajime targets equipment manufactured by Dahua Technologies (a known offender), the ZTE Corporation, and various other companies to which XiongMai Technologies had sold white-label DVR systems.
To avoid having equipment taken over by the Hajime worm, Rapidy Networks suggests three techniques to detect and mitigate infections: (1) block any UDP packet containing Hajime's key exchange message, (2) block TCP port 4636 used in Stage 1, and (3) block any traffic from Telnet sessions that execute the "/bin/busybox ECCHI" shell command.
As for who's behind Hajime, the Rapidity researchers have a theory: "Analysis of the file timestamps shows that the author is most active between the hours of 15:00-23:00 UTC, with no activity from 00:00-05:00 UTC. This roughly fits the sleeping pattern of an individual in Europe."
Furthermore, the team found evidence that work on Hajime started back in 2013, but that the worm was released in the wild only this past September.
"While both Hajime and Mirai use an extremely similar attack pattern when spreading to new hosts, the actual scanning and propagation logic appears to have been taken from qBot," Edwards and Profetis added. "If the above launch date estimate is correct [Mon, 26 Sep 2016 08:41:54 GMT], Hajime began operation a few days before the release of Mirai's source code, and is unlikely to contain any actual Mirai code."

 14 DAY TRIAL //
14 DAY TRIAL //