All the email leaks published on Hacking Team’s Twitter profile following the hijacking of the account have vanished as the company is once again handling the communication via this channel.
The account was under the control of the hackers for well over 10 hours, and it was used to distribute info from the stolen data cache. Before the company regained control, its profile looked like this.
Hacking Team is a known vendor of custom surveillance software, for any computer platform (mobile or desktop), to governments and equally deep-pocketed organizations.
The company’s headquarters are in Milan, Italy, and recently its systems were hacked by an unknown party, who chose to leak all the pilfered information amounting to some 400GB via torrent sharing.
The data started to drip into the public domain on Sunday evening, apparently without anyone from the company being aware of the activity.
Data dump is filled with viruses
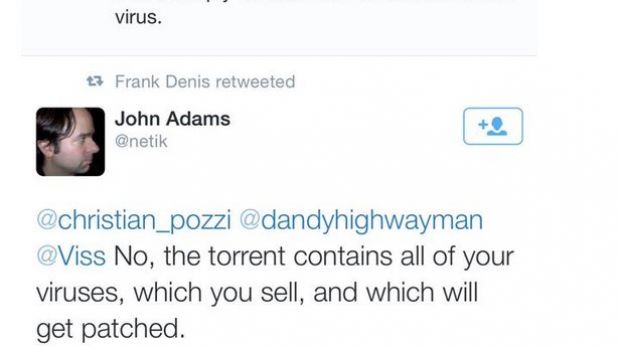
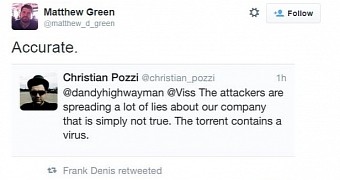
An engineer at the company, Christian Pozzi (whose Twitter account has been removed), tried to reduce the exposure by tweeting that the 400GB torrent file contains a virus and that the attackers just try to spread lies about Hacking Team.
Some security experts caught the message and were quick to agree, Matthew Green among them, a reputed cryptography professor at Johns Hopkins University, and John Adams, ex-operations and security guy at Twitter. They said that the malware included in the cache is the one developed by Hacking Team itself.
Hacking Team sold software to Sudan intelligence
On multiple occasions in 2012, Hacking Team’s CEO, David Vincenzetti told several publications that its customers are screened and that the company takes into account UN resolutions, international treaties as well as recommendations relating to human rights from adequate bodies.
However, the recently leaked documents show a September 2012 invoice from the company to the National Intelligence and Security Services in Sudan, for a second payment of $480,000 / €435,000. Evidence showing more recent business, from 2014, with Sudan has also been leaked on Hacking Team’s Twitter account.
According to security engineer @bcrypt, in the email correspondence from the company there is talk about cross-browser exploits being for sale, which could be leveraged for infecting systems.
The engineer also says that Christian Pozzi’s password for the Gmail account was changed some six hours ago, which is consistent to the time Pozzi started issuing “warnings” about the alleged malicious state of the 400GB torrent, hoping that people would stop downloading it.
A Pozzi scheme is a fraudulent assertion that a torrent you are downloading contains a virus and opening it will lead to jail.
— Dehickensian (@securedmh) July 6, 2015
 14 DAY TRIAL //
14 DAY TRIAL //