Leveraging a technique called "masquee attack," the Hacking Team has managed to find a way to tap into and then steal data from a series of popular iOS social and messaging applications.
The masquee attack is a procedure through which attackers can overwrite official, verified iOS applications, with one of their own.
Discovered back in December 2014 and later patched by Apple with the release of iOS 8.1.3, masquee attacks have never got to cause any problems to iOS users. Until now.
The first instance of a weaponized masquee attack
Sifting through data from the Hacking Team leak, FireEye researchers have discovered that the Italian-based cyber-intrusion company has found a way to utilize masquee attacks in real-world scenarios.
The US security firm confirms that the Hacking Team was able to break down 11 popular iOS apps, adding an extra binary to their official package, without being detected.
This binary would allow them to tap into the user's activity inside that app, and if desired, send various types of data, from the user's phone to a remote server without any kind of user interaction.
The 11 apps that were used by the Hacking Team are as follows: WhatsApp, Twitter, Facebook, Facebook Messenger, WeChat, Google Chrome, Viber, Blackberry Messenger, Skype, Telegram, and VK. We counted 12, but probably the researchers thought Facebook and Facebook Messenger as the same app. We're not going to argue with that.
From these apps they were able to record voice calls, intercept IM conversations, tap into calls, read SMS messages, get geolocation data, get recent photos, retrieve the user's contacts, and view what pages the user has last visited using the Chrome browser.
It was very hard for non-technical users to distinguish between the original and the malicious versions of the infected apps
According to the security researchers, the Hacking Team's masquee attack was very well coded to blend in as much as possible with the original applications, but there were a few signs that users could notice that the applications weren't behaving normally.
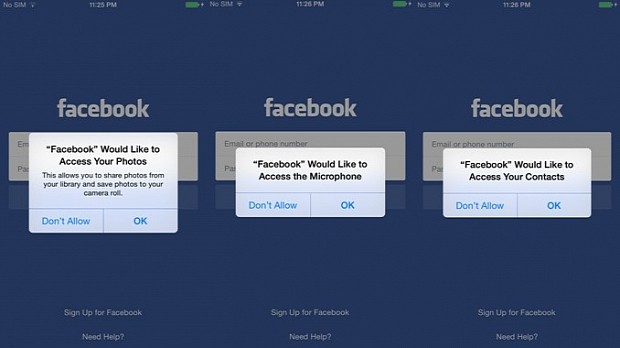
As an example, when the Facebook app was replaced with the infected version, when starting the app for the first time, three consecutive popups would appear, asking the user for permissions to access the phone's photos, microphone and contacts data.
Luckily, with iOS 8.1.3, Apple has made it impossible for apps that have the same bundle identifiers to replace themselves, but as researchers also point out, this won't stop attackers from installing the modified official apps on their own, without rewriting the original, hoping that users remove the official app and leave theirs on the system instead.
For the fine technical details, you can go on FireEye's blog and get more info on the steps an attack went through.
 14 DAY TRIAL //
14 DAY TRIAL //