A Reddit user has uncovered a covert method of carrying DDOS attacks on 4chan's infrastructure using images hosted on Imgur, via Reddit.
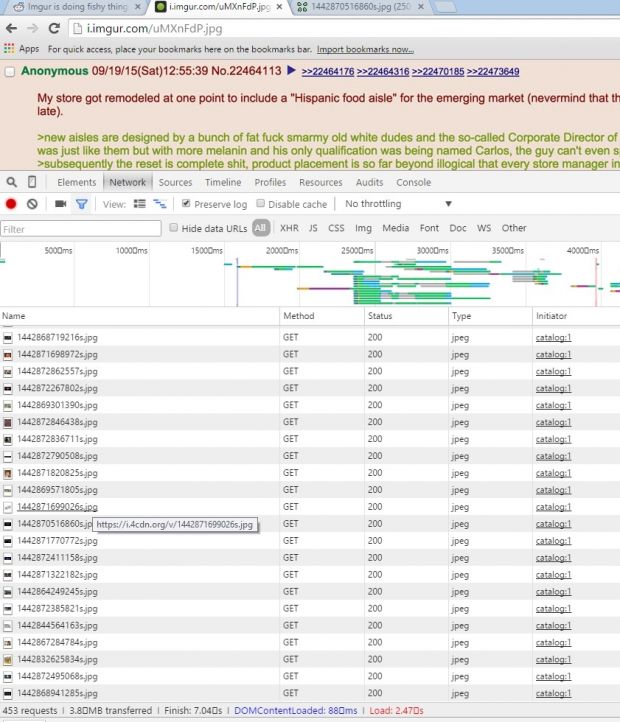
According to Reddit user rt4nyp, who discovered the vulnerability, every time an Imgur image was loaded on the /r/4chan sub-reddit, over 500 other images were also loaded in the background, images hosted on 4chan's CDN.
Since traffic on 4chan is quite huge as is, getting some extra connections from Reddit pushed 4chan's servers over the edge, crashing them several times during the day. Additionally, 8chan, a smaller 4chan spin-off, was also affected and suffered some downtime as well.
Malicious code was being loaded with Imgur images
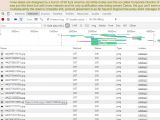
Reddit user rt4ny was alerted that something was amiss when he noticed that Imgur images on Reddit were loaded as inlined base64 data. Taking a closer look at the base64 code, he observed that a small piece of JavaScript code was added at the end, which had no business being there.
This code secretly stored the "axni" variable in the browser's localStorage, which was set to load another JavaScript file from "4cdns.org/pm.js." This is not 4chan's official CDN, but a domain registered to closely resemble the real deal, which was taken down in the meantime.
When refreshing the original image that loaded the "axni" variable, the malicious code would not be loaded again, a measure taken to avoid detection.
Additionally, also to avoid detection, the JS file stored on "4cdns.org/pm.js" could not be loaded directly in the browser.
Loading 500+ 4chan images inside a hidden iframe
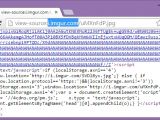
Analyzing the pm.js file, rt4ny found that it loaded an iframe outside the user's view with the help of some clever CSS off-screen positioning tricks, inside which the hundreds of 4chan images were being loaded, along with a 142 KB SWF file.
Imgur was contacted about this issue, and fixed it on the same day.
"Yesterday a vulnerability was discovered that made it possible to inject malicious code into an image link on Imgur," said the Imgur team. "From our team’s analysis, it appears the exploit was targeted specifically to users of 4chan and 8chan via images shared to a specific sub-reddit on Reddit.com using Imgur’s image hosting and sharing tools."
It's a sad day for humanity when we see hackers combine the three best sites on the Internet to find cat GIFs into such wicked and immoral ways.
@GranPC Hi there, thanks for bringing this to our attention, we're currently working on a solution.
— Imgur (@imgur) September 21, 2015
.@skooooch @imgur pic.twitter.com/HB9WzCXzQ9
— Gran PC (@GranPC) September 21, 2015

 14 DAY TRIAL //
14 DAY TRIAL //