A group of hackers, previously involved in various hacktivism campaigns, have accidentally made their way into an ICS/SCADA system installed at a water treatment facility and have altered crucial settings that controlled the amount of chemicals used to treat tap water.
This strange hacking incident is described in Verizon's 2016 Data Breach Digest (page 38, Scenario 8), a collection of case studies that the company's RISK team was brought in to investigate.
The victim of the hack is a company that Verizon identified under the generic name of Kemuri Water Company (KWC). As the RISK team explains, the company noticed that, for a couple of weeks, its water treatment center was behaving erratically, with chemical values being modified out of the blue.
Suspecting something was wrong - and something that its IT staff wasn't able to spot - the company brought in Verizon's RISK team to investigate.
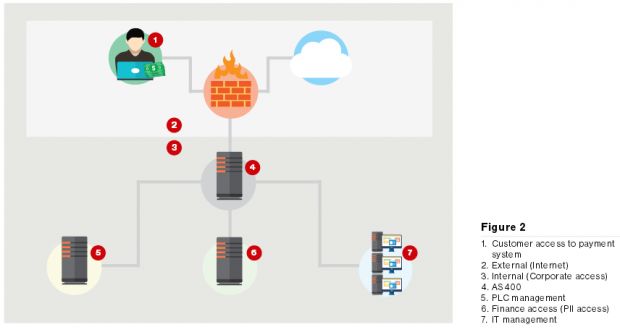
KWC was exposing its internal network to the Internet
Right from the get-go, the RISK team identified a series of issues. First off, KWC was using extremely outdated computer systems, some of which were running ten-year-old operating systems.
Additionally, the entire IT network revolved around a single equipment, an AS400 system, which would interconnect the company's internal IT network and the SCADA systems that managed the water treatment facility (a big no-no in terms of security).
Even worse, the same AS400 was also exposed to the Internet because it was routing traffic to a Web server where KWC's customers could check their monthly water bill, their current water consumption level, and even pay bills via a dedicated payments application.
But Verizon was about to get a bigger surprise because the company's investigation also discovered that there was only one KWC employee who could manage the AS400 system, meaning that cyber-intrusions when that employee was off-duty would have gone under the radar and could have easily crippled the company's activity.
Hackers had no clue what they were doing
After gathering all the basic network architecture details, Verizon RISK team moved on to inspect the AS400 equipment's logs. Comparing the IPs that accessed the device, security experts quickly found four instances of an IPs associated with hacktivism campaigns.
Looking deeper into the issue, the RISK team discovered that the hackers first breached the system via the Web-accessible payments application, looking for sensitive information about the company's clients.
It appears that the hackers discovered a vulnerability in the payments system, which they used to get access to the Web server, where they also found an INI file that contained administrative credentials, in cleartext, for the AS400 equipment.
Curious as they were, the hackers accessed the AS400 system, from where they also ended up on the SCADA system and started modifying parameters at random, unknowingly changing water treatment values.
Disaster was avoided due to secondary security measures
Secondary security measures allowed KWC to detect abnormalities in the levels of released chemicals, and aborted the hackers' instructions, but this happened often enough to arouse suspicions that this had to be more than a glitch.
"KWC’s alert functionality played a key role in detecting the changed amounts of chemicals and the flow rates. Implementation of a layered defense-in-depth strategy could have detected the attack earlier, limiting its success or preventing it altogether," the security investigation team concluded in their report.
After Verizon finished their investigation, the RISK team reassured that there was no malevolence from the hackers' side. They also informed the water treatment company that the hackers had access to over 2.5 million customer personal and financial records and provided technical expertise on how KWC could fix their IT system to prevent similar incidents.
A few weeks back, we also wrote about another hacking case from the same Verizon Data Breach Digest, where sea pirates hired a hacker to break into a shipping company's CMS to steal information about ship routes so they could plan their attacks and go only after the most valuable cargo.

 14 DAY TRIAL //
14 DAY TRIAL //