As a reminder that crooks will try everything to go undetected, Sucuri revealed last week a new method of inserting SEO spam on hacked WordPress sites using the /wp-includes/load.php file, one of WordPress' core files.
Unsecured WordPress sites are all around us thanks to the huge market share the CMS has compared to all other products. Crooks leverage this large number of unsecured sites to hack into WordPress installations, either via outdated plugins, vulnerable themes, or via weak admin passwords.
After hacking their target, crooks tend to use these sites as bots in DDoS attacks, as command and control servers for criminal operations, and as malware download sites, to host malvertising or hijack SEO results.
SEO spam relies on unsecured WordPress sites
They achieve the last by forcing hacked websites to load content that's hidden by default from human users but shows up for search engine crawlers.
These hacked websites present different text to search bots than what regular users would see, usually with completely different topics, descriptions, and links to other sites for which crooks want to boost search engine rankings.
This happens to the detriment of the hacked website, which now loses traffic and has its public description altered on Google, Bing or other sites.
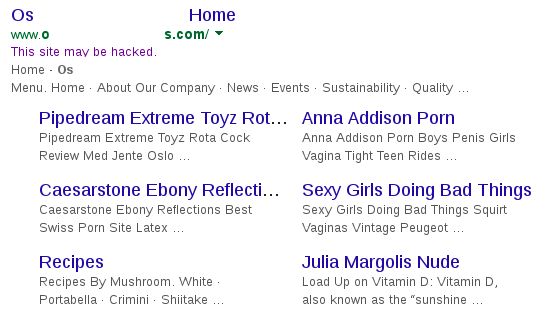
In one case Sucuri investigated, the company's analysts discovered a successful business portal showing pornographic content in its Google search results description.
Getting down to the bottom of the infection, Sucuri discovered that crooks weren't content with just loading a simple JavaScript or PHP file in the website's header or footer, but actually went as far as to modify WordPress core files, a place where very few site admins tend to look.
Crooks hijack WordPress core files to do all the dirty work
These particular hackers modified /wp-includes/load.php, a core WordPress file that runs for every site visitor and loads other files, putting together the final website.
"The attacker hopes you will focus on the theme files (i.e. header.php, footer.php) and the files in the root of the WordPress install (i.e. index.php, wp-load.php)," Sucuri's Luke Leal explains the crook's decision to modify this particular file.
Hackers modified /wp-includes/load.php to load another file /wp-admin/includes/class-wp-text.php, which should never exist in normal WordPress installations but which the crooks hid among other WordPress core files.
This, in turn, loaded all the SEO spammy content, but only for Google's search engine crawler, leaving the site as is for regular visitors. This procedure explains why the site showed up in search results as you can see in the image below but looked perfectly normal for everyone accessing it.
"At this point, I would like to mention that manually auditing your website files for modifications would be very exhaustive and this is why we recommend using file monitoring," Leal advises other site admins. "This system would alert you that a new file (./wp-admin/includes/class-wp-text.php) was created and a core file was modified (./wp-includes/load.php). Instead of having to manually go through over a thousand WordPress files, you already know which ones were modified and so can begin there."

 14 DAY TRIAL //
14 DAY TRIAL //