Security researchers have detected a new trojan targeting Android devices, but this one is unique in its own right because its creators have built it on top of an Android rooting utility called Root Assistant.
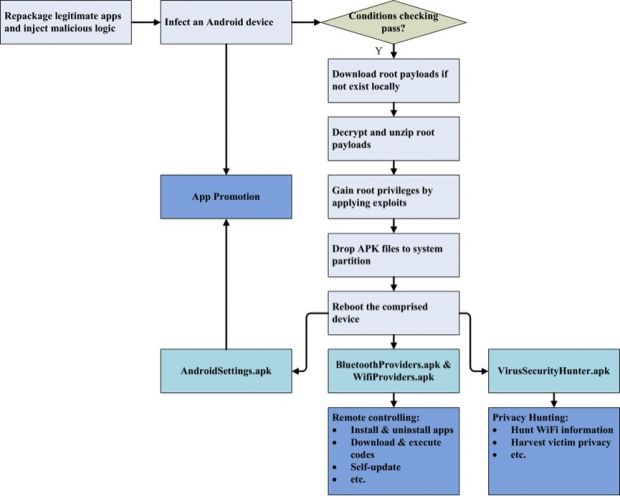
The new trojan, named Rootnik, takes the rooting toolkit's source code and twists it for malicious purposes, using it to gain root access without needing user interaction by leveraging the features packed inside the rooting toolkit.
Root Assistant was created a few years back by a Chinese company to allow users to root their devices using a single tap and four Android vulnerabilities (CVE-2012-4221, CVE-2013-2596, CVE-2013-2597, CVE-2013-6282).
There are at least 600 users infected with Rootnik
The people behind Rootnik took advantage of this app, decompiled its code, added their malicious code, and then added the final Rootkit trojan to the source code of other popular Android applications.
These apps were distributed through unofficial app stores and made their way onto at least 600 phones from countries such as the United States, Malaysia, Thailand, Lebanon, and Taiwan.
Palo Alto Networks, the security vendor that came across this threat, discovered the trojan in seven copies of legitimate applications like WiFi Analyzer, Open Camera, Infinite Loop, HD Camera, Windows Solitaire, ZUI Locker, and Free Internet Austria.
Besides pushing ads, Rootnik can also steal private data
After the trojan got root access to their device, the users that installed these contaminated applications found themselves pestered with ads, sometimes in fullscreen mode, and regardless of the currently active app.
Besides making a profit for its creators, the trojan can also perform other tasks. Rootnik can gain boot persistence on infected phones, download files on the device, install or uninstall apps on command, and steal private information such as WiFi SSID and BSSID identifiers, WiFi usernames & passwords, the phone's MAC, device ID, and the device's location.
Researchers first spotted Rootnik infections in February 2015. The trojan also comes with an XML file that prevents it from executing if the user is located in China. Only devices running Android 4.3 and earlier are vulnerable.

 14 DAY TRIAL //
14 DAY TRIAL //