Towards the end of last week, news broke of a secret backdoor in Juniper NetScreen firewall equipment running the ScreenOS operating system that would allow attackers to take control of the device and decrypt VPN traffic.
After experts dug through the operating system's code to take a closer look at the piece of "unauthorized code," as Juniper itself described it, they were able to uncover its password, made to look like a comment in the code.
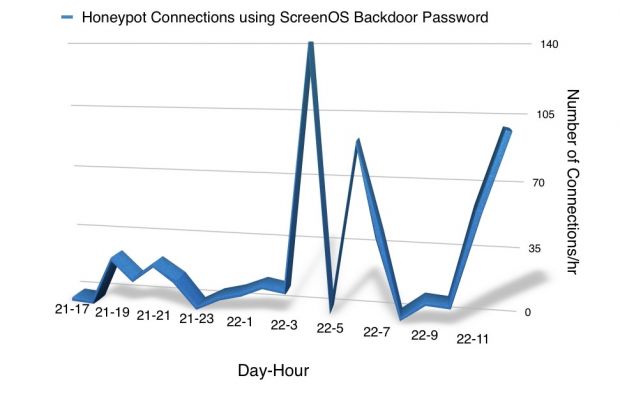
Soon after this, security researchers from the SANS Technology Institute’s Internet Storm Center (ISC) set up a honeypot trap server that mimicked a NetScreen device to see if something happened to it.
Honeypot server shows hackers' interest in Juniper firewalls
"We are detecting numerous login attempts against our SSH honeypots using the ScreenOS backdoor password," said ISC's Johannes B. Ullrich.
"Our honeypot doesn't emulate ScreenOS beyond the login banner, so we do not know what the attackers are up to, but some of the attacks appear to be 'manual' in that we do see the attacker trying different commands," Mr. Ullrich also added.
With over 26,000 NetScreen devices that run the vulnerable versions of ScreenOS, this puts hundreds or thousands of companies at serious risk.
Clarifications on which devices are affected, and by what
In the meantime, Juniper also clarified which versions are affected by what vulnerability.
The administrative authentication bypass issue (CVE-2015-7755) seems to affect only NetScreen devices with ScreenOS 6.3.0r17 through 6.3.0r20.
On the other hand, the VPN decryption issue (CVE-2015-7756) affects ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20.
Both vulnerabilities seem to have made their way into the operating system's code around 2012. Many have speculated that, because the ScreenOS code was written by Chinese developers from Juniper's NetScreen division, based in China, this may not be an NSA backdoor, as previously thought.

 14 DAY TRIAL //
14 DAY TRIAL //