Just 24 hours after the Joomla project released version 3.6.4 of the Joomla CMS to fix two critical security flaws, attackers had already started poking for unpatched systems and then launched mass scans half a day later.
The two flaws they're trying to exploit are CVE-2016-8870 and CVE-2016-8869. The first allows remote attackers to create accounts on Joomla sites while the second allows them to elevate the account's privileges to admin level.
While initially the Joomla team and Davide Tampellini, the Joomla engineer who discovered the latter flaw, refused to release any technical details about the flaw, many researchers have reverse engineered the 3.6.4 release, extracted the modifications, deducted the exploit methodology, and created numerous weaponized exploits they released online.
Mass scans coming from Romania and Latvia
Sucuri, who reverse engineered the 3.6.4 patch on its site, also created proof-of-concept exploitation code, which it embedded in its web firewall product.
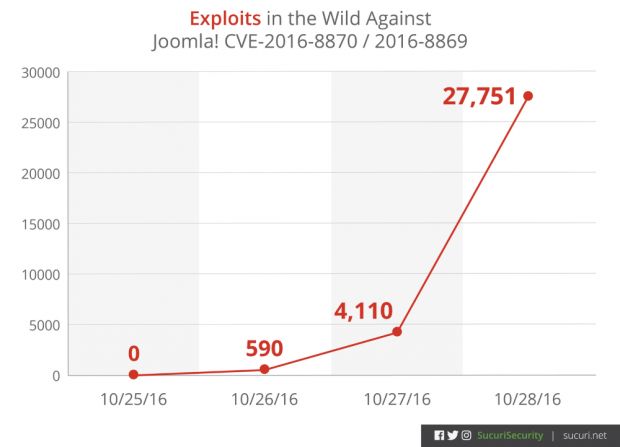
With the ability to detect exploitation attempts for these two flaws, Sucuri says that around 24 hours after Joomla released version 3.6.4, they saw three IPs from Romania prodding a few of the largest Joomla sites around the world.
The attackers were trying to exploit the two bugs by creating a user with the "db_cfg" name and the "fsugmze3" password.
Twelve hours after that, the three IPs moved from timid scans to full-on mass scanning and exploitation of any Joomla site they could identify.
Shortly after, a second actor using a Latvian IP started his own mass scans as well, creating randomly named user accounts on compromised sites with the "[email protected]" email address.
82.76.195.141
82.77.15.204
81.196.107.174
185.129.148.216
Sucuri recommends that site admins search their access logs for the above IP addresses. Attackers would generally attempt to access the following URL: "/index.php/component/users/?task=user.register"
Sucuri: Unpatched Joomla sites most likely compromised by now
"[I]t’s our belief that any Joomla! site that has not been updated is most likely already compromised," says Daniel Cid, Sucuri Founder and CTO.
"If you have not updated your Joomla site yet, you are likely already compromised," Cid adds. "Every Joomla site on our network was hit (and blocked by the Sucuri Firewall) and I assume pretty much every site out there suffered the same way."
The exact same thing happened last year, when the Joomla project patched zero-day CVE-2015-8562 in version 3.4.6, launched in mid-December. By the end of the year, attackers were launching on average around 16,600 scans per day, trying to exploit the flaw.

 14 DAY TRIAL //
14 DAY TRIAL //