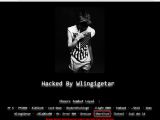
Because defacing websites is a waste of time and unsatisfactory, from a financial point of view, an Indonesian hacker has turned to writing his own PHP-based ransomware, which he's now deploying on the websites he was previously defacing.
The hacker in question is an Indonesian teen that goes by the name ShorTcut (or Shor7cut) and is a member of a hacking crew named Indonesia Defacer Tersakiti.
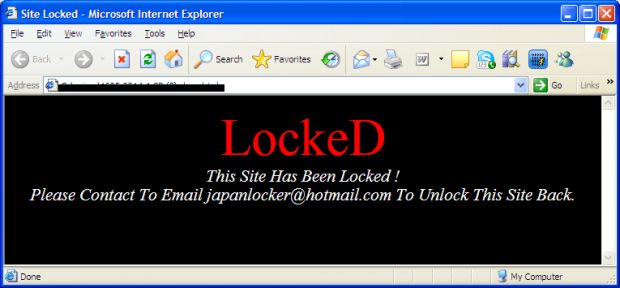
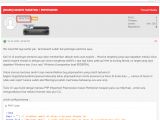
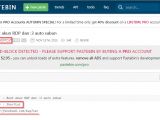
The hacker's new activities came to light when Fortinet researchers were investigating a website on which someone installed a PHP-based ransomware called JapanLocker. Researchers named it so because it was asking victims to contact the crooks for payment via the address [email protected].
Hacker is Indonesian, has nothing to do with "Japan"
While searching for clues on this new ransomware, Fortinet researchers discovered past versions of this threat where the author forgot to modify the email address, which appeared as shor7cut@localhost.
This is how Fortinet researchers found themselves investigating ShorTcut's past defacement activities, and how they discovered him sharing various exploits and scripts on Indonesian hacking forums.
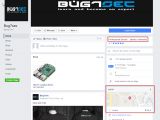
In the source code of one of those exploits, they found the URL of a Facebook page called bug7sec, that looked to advertise the services of a Jakarta-based IT company.
Hacker had open-sourced his ransomware on GitHub
The homepage of this company, as listed on the Facebook page, was a GitHub account, also named bug7sec. Here, Fortinet researchers discovered several repositories hosting hacking tools, mostly backdoors, but also a project named simply "ransomware."
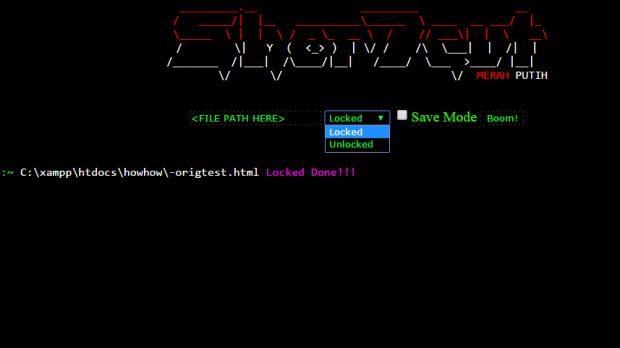
The project contained two folders, marked "v1" and "v2," each with a different open source ransomware. It didn't take long for Fortinet to identify the ransomware stored in the v1 folder, nicknamed "shc Ransomware," as the version from which ShorTcut derived JapanLocker.
Fortinet researchers investigating shc's capabilities (and inherently JapanLocker's) found that the ransomware worked by encrypting data with a combination of base64 encoding, ROT13 encryption, and top-bottom swapping.
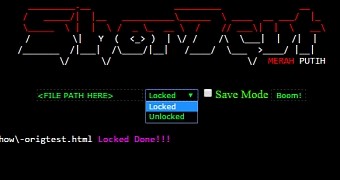
To deploy the ransomware, ShorTcut had to break into servers and run the installer, which is a simple point-and-click page.
Free decrypter available
With full access to the source code, Fortinet researchers reversed the encryption process, and have published a free decrypter that can unlock JapanLocker infections.
Overall, the ransomware is a simplistic tool, but all web-based ransomware families are simple and inefficient when compared to variants that target computers.
Also during their investigation, Fortinet researchers stumbled upon a YouTube video where it appears that ShorTcut had inadvertently exposed his real IP address, something which Indonesian law enforcement authorities will surely find interesting.
 14 DAY TRIAL //
14 DAY TRIAL //