Hackers have infected several US military and other government agencies with a stealthy piece of malware called GovRAT, created specifically for spying on high-value targets.
First discovered in November 2015 by InfoArmor, the GovRAT malware is a remote access trojan (RAT) sold on the Hell forum and TheRealDeal Dark Web marketplace.
The malware coder's nickname is bestbuy, but after InfoArmor released its first report, he started using and selling the malware under the Popopret nickname as well.
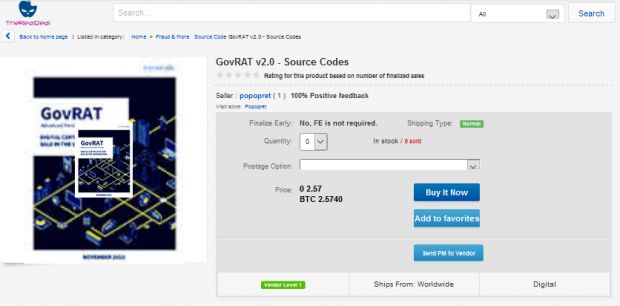
GovRAT 2.0 sold online for around $1,600 and more
The malware, which was recently updated to v2.0, is very advanced, based on its capabilities. The crook selling it has intentionally named it this way, to target a specific niche of hackers who go after government agencies primarily.
According to a recent listing on TheRealDeal, GovRAT's price is 2.5740 Bitcoin (~$1,600), but users can also buy access to the malware's source code for $6,000.
Two famous hackers working together
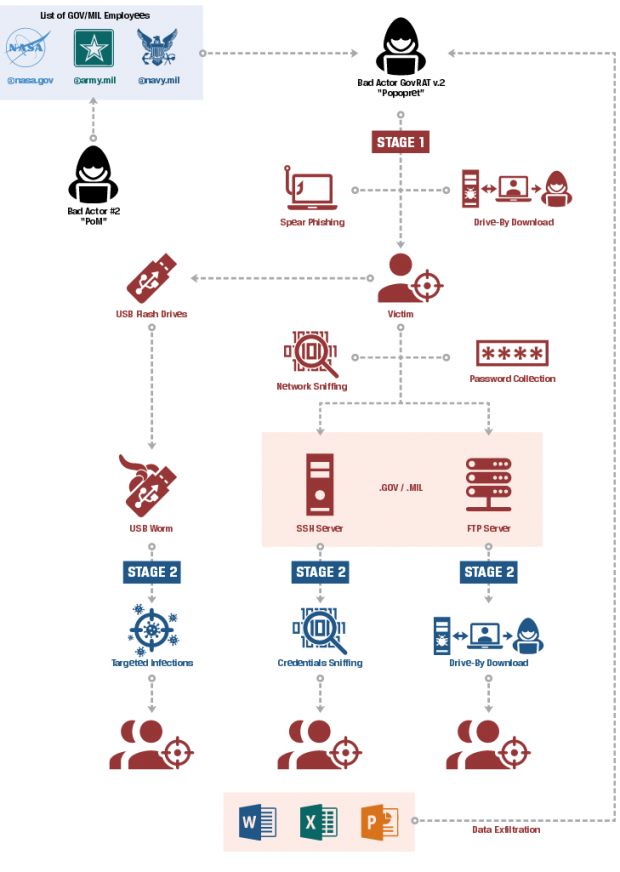
In a recent report, InfoArmor says that Popopret is working together with another hacker named PoM (Peace_of_Mind), who is distributing separately a series of files containing the emails and credentials for various types of accounts used by US military and government agencies.
PoM's list is comprised of over 33,000 records, with the majority of credentials coming from the US General Services Administration, the US Navy, and several big-name US universities such as USC, Missouri, and the University of Florida. At the time of writing, this listing is not active anymore.
Why is this important? InfoArmor says that a buyer would be encouraged to buy this list because they would need it to spam government officials, in order to distribute the malware as a file attachment, or to lure victims to a website serving GovRAT 2.0 via a drive-by download.
Additionally, InfoArmor says Popopret is also working with sellers of fake digital certificates, sending clients their way so they could sign and hide GovRAT from antivirus engines.
Once a target is infected with GovRAT, InfoArmor says the attackers can use it to sniff on the local network, or use the malware to dump passwords from the infected computer's apps.
This data can then be used to spread to nearby servers, from where they can infect more victims. GovRAT allows its buyers to use it and access an infected host, search for crucial files and then exfiltrate stolen data to a remote server.
GovRAT 2.0 can also deploy USB worms to USB flash drives, which will infect any other PCs the flash drive is plugged into. This functionality is used for jumping from target to target on air-gapped networks.
Here are the features Popopret says GovRAT 2.0 possesses, as written by the hacker himself on TheRealDeal.
Features:
- Access C&C with any browser.
- Compile C&C for Linux OR Windows.
- Cannot be reversed without the private key. 0day anti-debugging.
- Automatically maps all hard disks and network disks.
- Creates a map of files to browse even when the target is offline.
- Remote shell / command execution.
- Upload files or Upload and Execute files to target.
- Download files from target. All files are compressed with LZMA for faster downloads and encrypted on transport.
- Customized encryption for communications. No 2 machines will use the same key (ever).
- SSL Support for communication. (you have to get your own *Valid* SSL certificate to use this).
- Does not use socks libraries. Uses special windows APIs to communicate and cannot be blocked.
- C&C Creates a One-Time-Password every time you login for extra security.
- Comes with source for FUD keylogger that sends keys to another server.
- Excellent for long term campaigns where a stable connection is needed.
Updates:
- %100 FUD Again after bluecoat discovered the RAT.
- Network spreading module (using ARP/MITM to hijack all exe downloads) - turn on and off with 1 click.
- Endpoint bypass
- 360 bypass
More updates (28th of April 2016):
- Browser password dumper (all common browsers)
- Mail password dumper (all common mail clients)
- Cleartext network password sniffer (many modules including http, ftp, imap, pop3, etc...)
- Network shares password dumper (saved passwords)
- USB Spread with 2 options (1. fake shortcut method, 2. DLL Hijacking of common applications based on private list and research)
- TOR onion domain support added !
"The organizations targeted by the GovRAT v2.0 malware primarily conduct their operations in English," InfoArmor writes in its most recent report.
"However, several samples with non-English signatures for data exfiltration related to names of the documents, their security classification, author and additional details have been identified," the company also reveals.
Both hackers have been linked to a series of mega breaches
Popopret is more famous for his previous nickname, bestbuy, being behind some serious data breaches hitting Dark Web marketplaces, such as the Thomson Reuters World-Check database of suspected terrorists.
PoM, or Peace, or Peace_of_Mind, is as well-known as bestbuy, previously putting up for sale data from breaches at companies such as Yahoo, LinkedIn, Tumblr, and VK.
Both hackers are not behind these mega breaches, but they made a name for themselves by selling the data than by creating and selling GovRAT.

 14 DAY TRIAL //
14 DAY TRIAL //