A new ransomware strain (7ev3n), seen for the first time last week, combines old-school ransomware tricks with newer crypto-ransomware tactics to force users into paying the ransom fee in order to unlock both the files and the computer.
When ransomware appeared for the first time, it did not encrypt files as modern crypto-ransomware families do. Most of the time, older ransomware versions worked by showing a message that covered the entire screen and prevented the user from interacting with other apps and OS functions.
But when crypto-ransomware appeared, all these (older) features that prevented a user from interacting with the operating system were dropped, mainly because they were useless, since the user couldn't access their files anyway.
This is because, in almost all crypto-ransomware incidents, the ransomware encrypts files and leaves a ransom note in the form of a .txt or .html file in the file's same directory. Often, you'll also see the ransomware change the user's screen, or show a pop-up overlaid on top of the screen, but never preventing the user from interacting with other applications.
The thinking behind this was to allow the user to connect to the Internet, register a Bitcoin account, and make the payment to the crypto-ransomware's owner.
7ev3n ransomware combines the old with the new
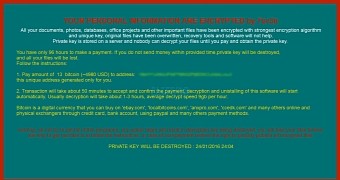
Two things are unique and strange about this newer 7ev3n ransomware family. First off, it asks for an exorbitant amount of money. 13 Bitcoin is about $5,000, or €4,600, a sum that very few people can afford.
Secondly, the ransomware employs old school tricks to block the user's computer. It achieves this by using a combination of .bat files that alter registry keys and disable the F1, F10, F3, F4, Enter, Escape, Left Alt, Left Ctrl, Right Alt, Right Ctrl, Right Shift, Left Windows, Right Windows, Num Lock, and Tab keys.
Without these keys, it is almost impossible to remove the ransom note from the screen by non-technical users. Even if paying the ransom, most users would need to hire professional help to restore the computer to its previous working state and then recover all the files.
For technical users, the Bleeping Computer staff put together a simple step-by-step tutorial on how to remove the ransom note from the screen. To unlock the encrypted files, users will still have to pay the ransom, since 7ev3n's encryption has no visible flaw to allow an easy and quick decryption.
For now, only one person has reported a 7ev3n ransomware infection, but his case was interesting because the ransomware seems to have hit a Windows server and propagated from there to other computers.
Besides the unremovable lockscreen, the other telltale sign that you've been hit by 7ev3n is that all your files have been encrypted and renamed with the .r5a file extension.
 14 DAY TRIAL //
14 DAY TRIAL //