Maxime Kjaer, a 19-year-old Danish student, has uncovered a set of Google Chrome extensions that were hijacking Facebook accounts but were capable of many more malicious actions.
Crooks were distributing these extensions via Facebook posts for all sorts of cheesy and raunchy viral content. Users who clicked on the links inside those Facebook posts landed on a site that asked them to verify their age.
Unlike other sites that allowed users to enter their age in a form, these ones were asking them to install one of many Chrome extensions.
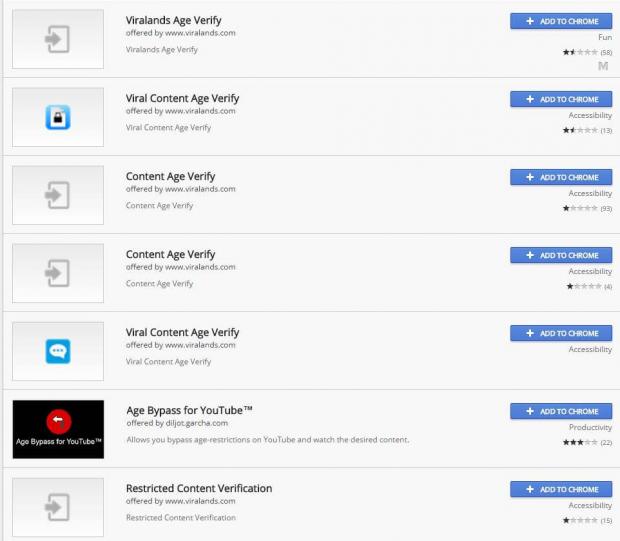
Extensions were hosted on the Google Chrome Web Store
All of these extensions had a similar name, involving the words "viral," "age," and "verify," and were hosted on the Google Chrome Web Store, which helped users dispel any doubts they had about the extension's legitimacy.
Kjaer, who broke down the code found inside one of these extensions, explains that they all requested intrusive permissions, such as the ability to "Read and change all your data on the websites you visit," giving it complete control of a user's visited sites.
The extension itself contained only three files, which Kjaer said they executed in persistent mode. This means they couldn't be paused and executed from when the browser started until the user shut it off.
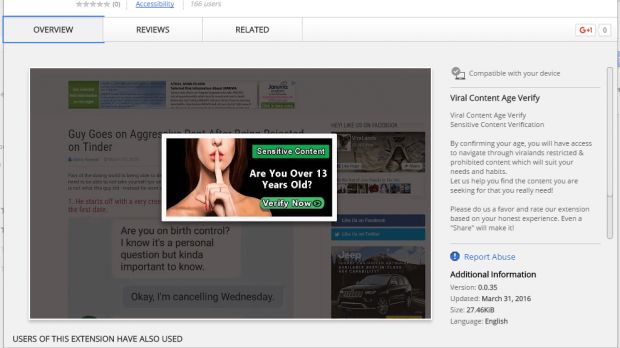
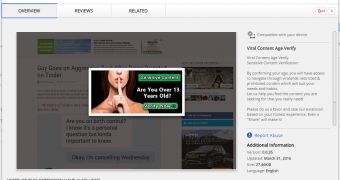
There was no age verification process, just malicious operations
The first file in these extensions was background.js, the script that did the actual age verification process. Kjaer says that there was no "less than 18" verification process and that the source code found inside this file only started a random timer after the user filled in their date of birth, and then showed "Loading..." during the timer and "Done!" at the end.
The second file, query-string.js, was only a clone of an NPM module of the same name, which was used for the third file, install.js.
This third file was where all the malicious activity could be found. This script would connect to a server and download another script, which it would later execute.
This is common practice across malicious Chrome extensions, which, because of Google's automated scans when submitting extensions to the Chrome Store, can't include malicious code in the original extension source, so they download it at a later stage.
Crooks used a C&C server to control infected browsers
In the malicious code Kjaer received, he says the downloaded script would be able to make requests and receive instructions from a command and control (C&C) server.
During his experiment, the C&C server told his browser to access a Facebook URL that exposed his access token, a programmatic key to his Facebook account.
Because of the "Read and change all your data on the websites you visit" permissions the user has granted the extension at installation, the crook was able to recover this access token.
The download script reported this access token to the C&C server, which would be able to access the user's account on their behalf. As soon as their access token was stolen, the C&C server instructed the user's browser to give a Like to a Facebook Page Kjaer had never seen before.
Extensions gave crooks complete control of the browser
While only this attack was carried out under Kjaer's watchful eyes, the developer says that the C&C server can literally order the browser to do anything it wants.
A small list of possible actions includes the ability to log password keystrokes, subscribe to YouTube channels, execute DDoS attacks, mine for Bitcoin, read emails, and anything else that could be accomplished via a Chrome browser.
According to Kjaer's calculations, 132,265 infected computers had installed the malicious Chrome extensions.
The researcher reported the IP addresses used to download the malicious script payload and the C&C servers to Digital Ocean, the company that was hosting the servers.
He also informed Google, who removed the extensions from the Chrome Web Store and then blacklisted them, which means they were automatically uninstalled from all infected browsers.
 14 DAY TRIAL //
14 DAY TRIAL //