A total of 36 fake security apps for Android that were published in the Google Play Store were used to secretly harvest user data from devices and push intrusive ads.
Discovered by security company Trend Micro, the apps (PDF document) have already been removed by Google last month, though at this point it’s not known how many downloads they recorded during the time they were available in the Google Play Store.
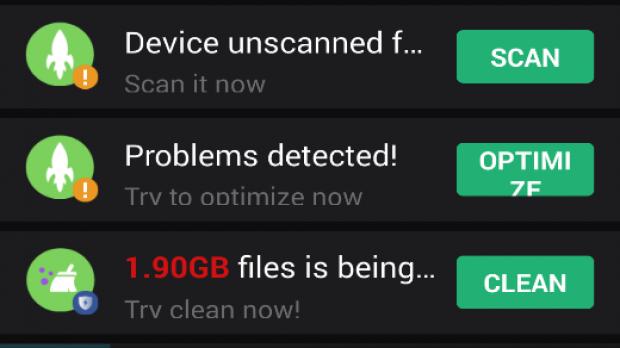
An in-depth look at their behavior reveals that these apps claimed to offer scanning features, cleaning junk, or features to save battery, cool the CPU, or lock apps.
“The apps were actually able to perform these simple tasks, but they also secretly harvested user data, tracked user location, and aggressively pushed advertisements,” Trend Micro’s Lorin Wu, Mobile Threats Analyst, explains.
User data uploaded to remote server
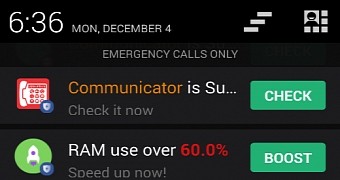
The first sign of malicious behavior was detected right after the apps were installed, as no shortcuts were created on the home screen or in the app list. Instead, they were completely hidden and only pushed notifications that included fake alerts prompting various actions and only “used to add a layer of legitimacy to the app,” the security expert adds. Fake animations were displayed with no legitimate process running in the background in an attempt to convince users of the efficiency of the apps.
Interestingly, these apps were developed to not run on new-generation Android devices like the Nexus 6P, most likely in an attempt to avoid being detected by Google Play Protect or other security features that might exist on such models.
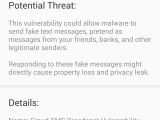
In addition to bombarding devices with ads, the apps were also capable of collecting user data and uploading it to a remote server. The user information that was collected includes Android ID, Mac address, OS version, brand and model of the device, location, app data like Facebook, and notifications.
“The app is able to upload user data information, installed app information, as well as attachments, user operational information, and data on activated events to a remote server,” Wu notes.
More sensitive information like SMS messages, photos, and banking data is believed to have been exposed to the malicious apps.
 14 DAY TRIAL //
14 DAY TRIAL //